April 10, 2024 at 09:15AM
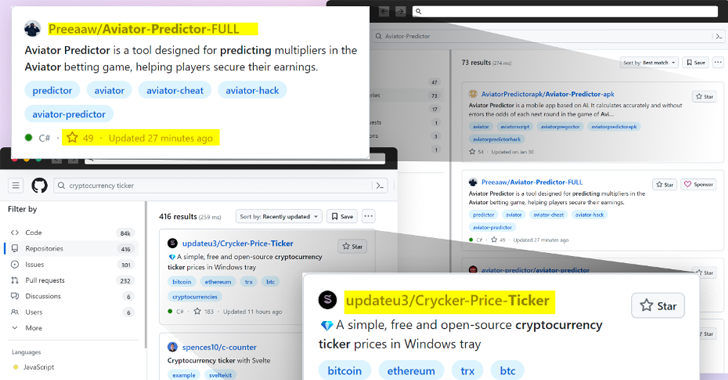
Threat actors are leveraging GitHub’s search feature to dupe users into downloading malicious code by creating fake repositories with popular names. The attackers manipulate search rankings and use fake stars to deceive users. Researchers warn of the ongoing threat to the open-source ecosystem and emphasize the need for caution when downloading from such repositories.
Based on the meeting notes, it is clear that threat actors are manipulating GitHub’s search functionality to distribute malware through malicious repositories. The attackers are taking several measures to deceive users, such as creating repositories with popular names, using fake stars to boost rankings, and disguising the repositories as legitimate projects related to popular games, cheats, and tools. It’s also mentioned that malicious repositories have been observed downloading encrypted files containing executable malware.
Moreover, the notes highlight the significance of developers exercising due diligence when downloading source code from open-source repositories and emphasize the dangers of solely relying on reputation as a metric to evaluate trustworthiness.
Another point of the discussion involves the discovery of an increase in spam packages being published to the npm registry, indicating a non-malicious campaign abusing the Tea protocol for automated crypto farming.
Overall, the meeting notes underscore the ongoing threat posed by the use of malicious GitHub repositories to distribute malware and the need for developers to be vigilant in their source code downloading practices.