October 26, 2023 at 04:48AM
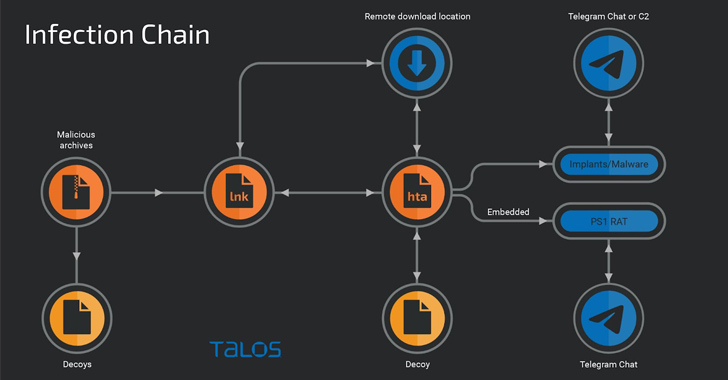
A new threat actor called YoroTrooper, likely consisting of operators from Kazakhstan, has been identified. The group employs various tactics to hide their activities, including targeting Kazakhstani entities and using VPN exit nodes in Azerbaijan. YoroTrooper primarily uses spear-phishing and malware to steal data, and has now shifted to custom tools programmed in Python, PowerShell, Golang, and Rust. They have targeted state-owned entities in CIS countries and utilize currency conversion and email accounts to carry out their operations.
Key takeaways from the meeting notes:
– A new threat actor called YoroTrooper, likely originating from Kazakhstan, has been identified.
– YoroTrooper uses various tactics to obfuscate the origin of their operations, including using VPN exit nodes in Azerbaijan.
– The group primarily relies on spear-phishing to distribute malware and steal data.
– YoroTrooper has recently started using custom tools programmed in Python, PowerShell, Golang, and Rust.
– The threat actor has strong ties to Kazakhstan and regularly scans the state-owned email service for vulnerabilities.
– YoroTrooper has been targeting state-owned entities in Commonwealth of Independent States (CIS) countries.
– They have been using email accounts to register and purchase tools and services, including a NordVPN subscription and a VPS instance.
– YoroTrooper has added Golang- and Rust-based malware to their arsenal, allowing them to establish a reverse shell and harvest sensitive data.
– The group uses Telegram for data exfiltration and command and control communication.
– YoroTrooper has been experimenting with different types of delivery vehicles for their backdoors.
Please let me know if you need any further information or if there’s anything specific you would like me to focus on.