April 26, 2024 at 10:18AM
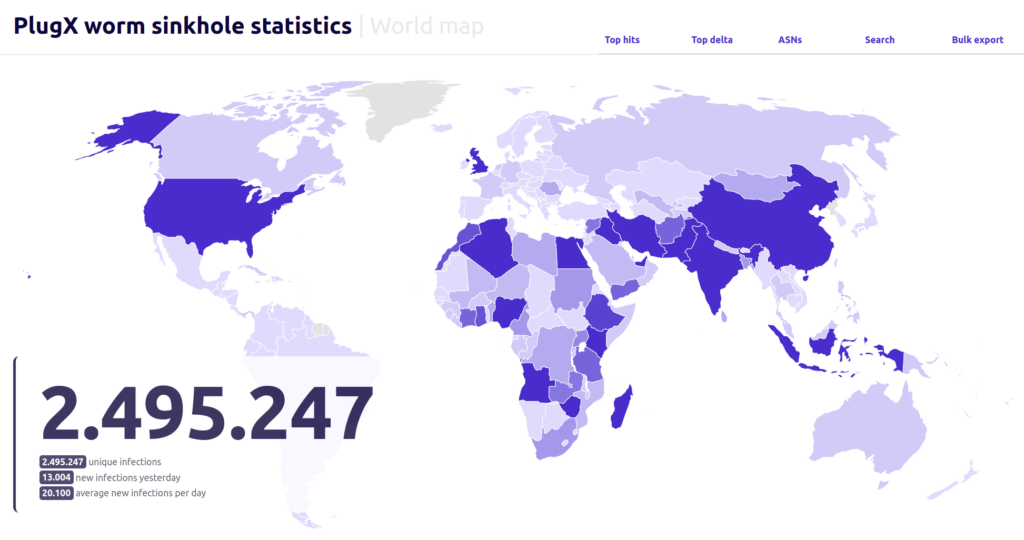
Sekoia reports that over 90,000 unique IP addresses are still infected with a self-spreading PlugX worm variant, attributed to a China-linked threat actor. The malware spreads through infected USB drives, creating potential risks for data exfiltration and surveillance, especially in regions strategically important to China’s Belt and Road Initiative. Sekoia is working with authorities to address the issue.
Based on the meeting notes, here are the key takeaways:
– Over 90,000 unique IP addresses are still infected with a self-spreading variant of the PlugX RAT, spread via infected USB drives, bypassing air gaps.
– The botnet continues to be active, even though its operators no longer have control over it.
– The self-spreading technique has led to an uncontrollable expansion of the botnet across networks, prompting its operators to abandon the command-and-control server.
– Sekoia was able to identify roughly 2.5 million infected hosts in over 170 countries worldwide, with the worm still spreading at an average of 20,000 infections per day.
– Most of the victims are in countries of strategic importance to China’s Belt and Road Initiative.
– The security firm has detected a self-delete command and a potential mechanism to deliver the command to infected hosts and remove the malware from them.
– Sekoia is in the process of contacting Computer Emergency Response Teams (CERTs) and law enforcement agencies in the affected countries to decide whether the disinfection should be performed.
If you have any other specific questions or need further details on any of the points, feel free to ask.