May 21, 2024 at 09:12AM
Persistent threat actors behind the SolarMarker malware have established a complex, multi-tiered infrastructure, making it challenging for law enforcement to take down. The malware targets various sectors and has evolved to enhance stealth and control over victim machines. Recorded Future’s investigation uncovered the architecture of the command-and-control (C2) servers.
After reviewing the meeting notes, the key takeaways are:
– SolarMarker is a persistent and sophisticated information-stealing malware with a multi-tiered infrastructure that complicates law enforcement takedown efforts.
– It exhibits continuous evolution and has the capability to steal data from web browsers, cryptocurrency wallets, and target VPN and RDP configurations.
– The top targeted verticals include education, government, healthcare, hospitality, and small and medium-sized enterprises, with the majority of victims located in the U.S.
– The malware authors have focused on making SolarMarker more stealthy through various means such as increased payload sizes, valid Authenticode certificates, and the ability to run it directly from memory.
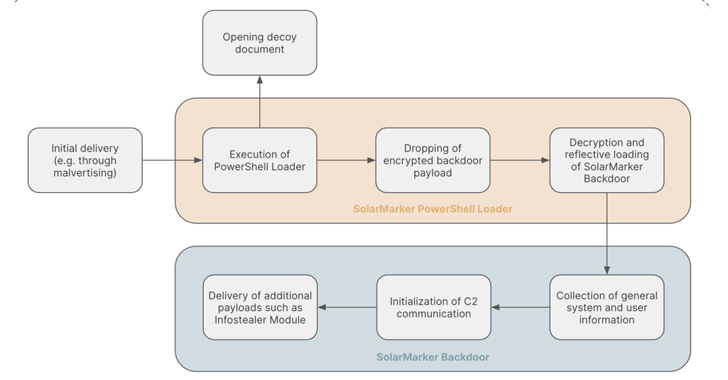
– Infection pathways typically involve hosting SolarMarker on bogus downloader sites or via malicious emails, and recent cases have involved the use of decoy files and alternate installers to propagate the malware.
– The malware is also associated with a Delphi-based hVNC backdoor called SolarPhantom, and its threat actor has alternated between different tools to generate payloads.
– There is evidence to suggest that SolarMarker is the work of a lone actor of unknown provenance, possibly with a Russian connection.
These are the key points from the meeting notes regarding the SolarMarker data breach and malware. If there are any specific actions or next steps to be discussed or if there are further details needed, please feel free to let me know.