November 25, 2024 at 07:33AM
Cybersecurity researchers have identified new attack techniques targeting IaC and PaC tools like Terraform and OPA, enabling data breach through unauthorized Rego policies. Attackers exploit vulnerabilities during CI/CD processes, emphasizing the need for strict access controls, logging, and IaC scanning to mitigate risks and prevent malicious activities in cloud environments.
### Meeting Takeaways: Cloud Security / Supply Chain Attack (Nov 25, 2024)
**Key Points:**
1. **New Attack Techniques Identified**:
– Cybersecurity researchers have reported vulnerabilities in infrastructure-as-code (IaC) and policy-as-code (PaC) tools, specifically HashiCorp’s Terraform and Open Policy Agent (OPA).
– The attacks exploit dedicated, domain-specific languages (DSLs) used in these tools.
2. **Understanding OPA and Its Risks**:
– OPA allows policy enforcement across cloud-native environments and evaluates policies using a native query language called Rego.
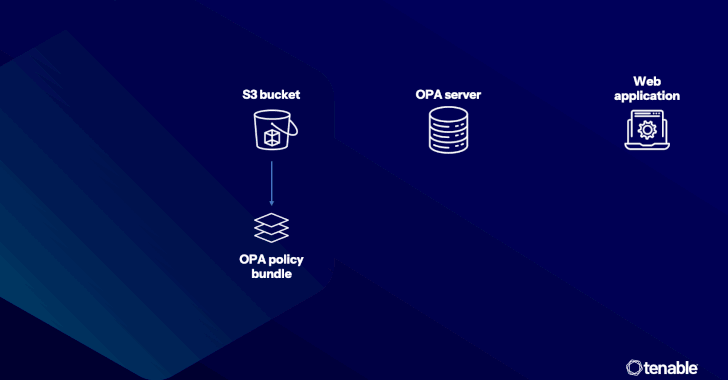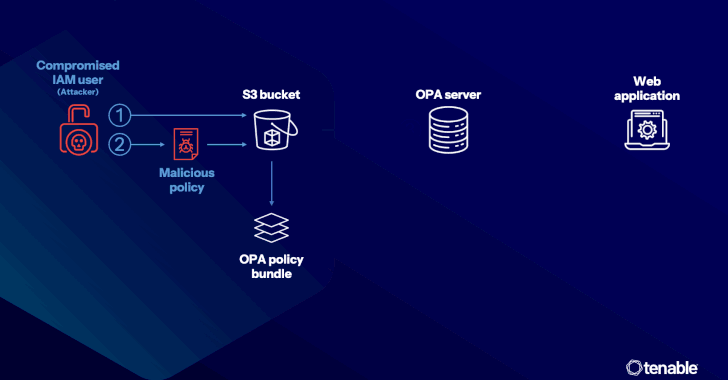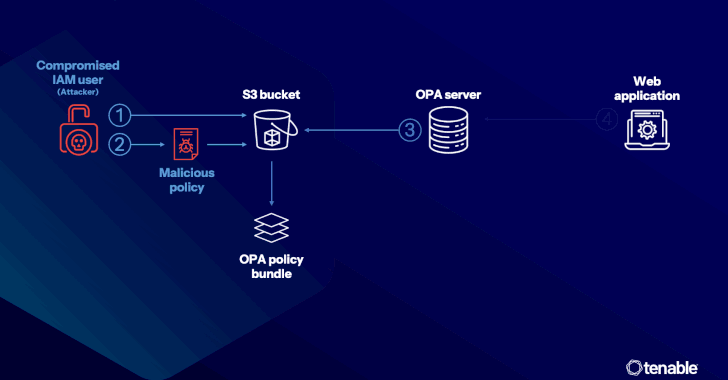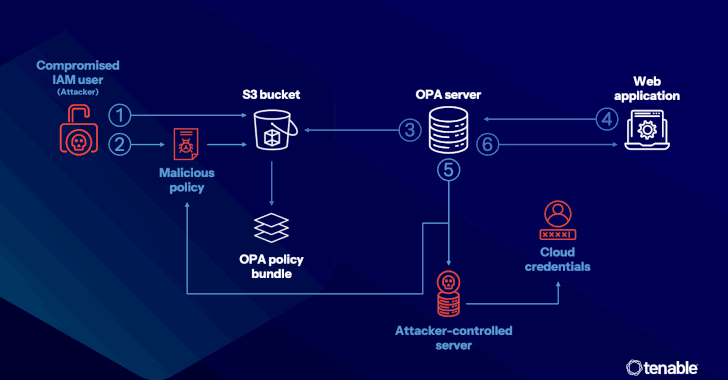
– Attacks can occur via compromised access keys that allow the insertion of malicious Rego policies, potentially leading to data exfiltration via functions like “http.send.”
– Even with restrictions on “http.send,” data can still be exfiltrated using “net.lookup_ip_addr” through DNS tunneling.
3. **Threats to Terraform**:
– Terraform configurations can be compromised during the “terraform plan” command, often executed as part of GitHub “pull_request” workflows.
– Malicious actions can be executed through unreviewed changes in public repositories or by insiders with access to private repositories.
4. **Mitigation Strategies Recommended**:
– Implement granular role-based access control (RBAC) and adhere to the principle of least privilege.
– Establish comprehensive logging at both application and cloud levels for better monitoring and analysis.
– Restrict network and data access for applications and underlying infrastructure.
– Prevent automatic execution of unreviewed code in CI/CD pipelines.
– Utilize IaC scanning tools like Terrascan and Checkov for early identification of misconfigurations and compliance issues.
**Conclusion**: Organizations must adopt stringent security measures and regularly review their access and deployment practices to safeguard against these emerging threats in cloud security and supply chain integrity.
*For more insights, follow us on Twitter and LinkedIn.*