October 16, 2023 at 01:12AM
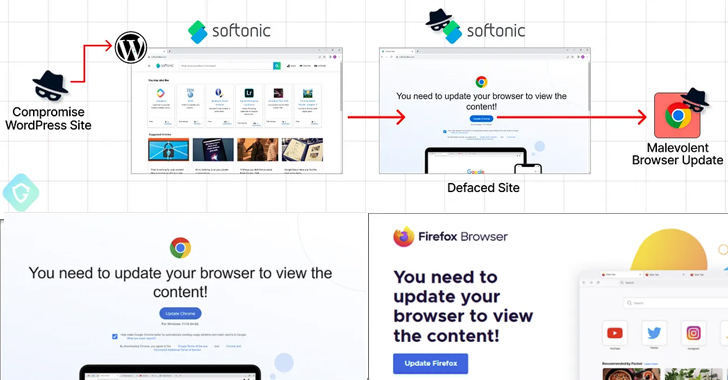
Threat actors are using Binance’s Smart Chain (BSC) contracts to host and deliver malicious code, making it difficult to detect and stop their attacks. The campaign, known as EtherHiding, leverages compromised WordPress sites to deceive users into downloading malware through fake browser update notices. The decentralized nature of blockchain makes it challenging to intervene. Users are advised to follow security best practices for WordPress, including regularly updating their systems and employing strong passwords.
Key Takeaways from the Meeting Notes:
1. Threat actors have been using Binance’s Smart Chain (BSC) contracts to serve malicious code, marking a new level of bulletproof hosting.
2. The campaign, codenamed EtherHiding, leverages compromised WordPress sites to display fake browser update warnings and deploy information-stealing malware.
3. Initially, the attackers hosted the code on abused Cloudflare Worker hosts, but they have now switched to utilizing the decentralized and anonymous nature of blockchain.
4. The infected websites are injected with obfuscated Javascript to interact with the BNB Smart Chain and retrieve a third-stage payload from a command-and-control server.
5. Clicking the update button on the fake overlay redirects victims to download a malicious executable from legitimate file hosting services like Dropbox.
6. The decentralized nature of the attack makes it difficult to intervene and disrupt the attack chain.
7. Users of WordPress should follow security best practices, keep their systems up-to-date, remove unwanted admin users, and use strong passwords to mitigate the risks associated with plugin vulnerabilities.
If you have any further questions or need additional information, please let me know.