December 14, 2023 at 08:00AM
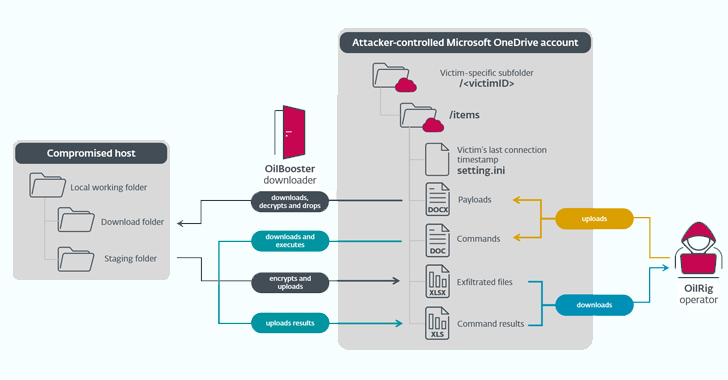
OilRig, an Iranian cyber espionage group, has deployed three new downloader malware named ODAgent, OilCheck, and OilBooster to maintain access to victim organizations in Israel. These lightweight downloaders use legitimate cloud service APIs for command-and-control communication, aiming to blend with authentic network traffic. The targets include healthcare, manufacturing, and governmental organizations.
The meeting notes cover the activities of the Iranian state-sponsored threat actor known as OilRig, who deployed three different downloader malware to maintain access to victim organizations in Israel. The downloaders, named ODAgent, OilCheck, and OilBooster, use legitimate cloud service APIs for command-and-control communication, with the goal of blending with authentic network traffic. The targets of the campaign include organizations in the healthcare sector, manufacturing, and local governmental organization, who have been previously targeted by the threat actor. The exact initial access vector is currently unclear, and it’s not known if the attackers managed to retain their foothold in the networks. OilRig has also been observed leveraging novel malware like MrPerfectionManager, PowerExchange, Solar, Mango, and Menorah this year. It’s noted that the downloaders use a shared OilRig-operated account to exchange messages with the operators, and the same account is typically shared by multiple victims.