January 24, 2024 at 02:00AM
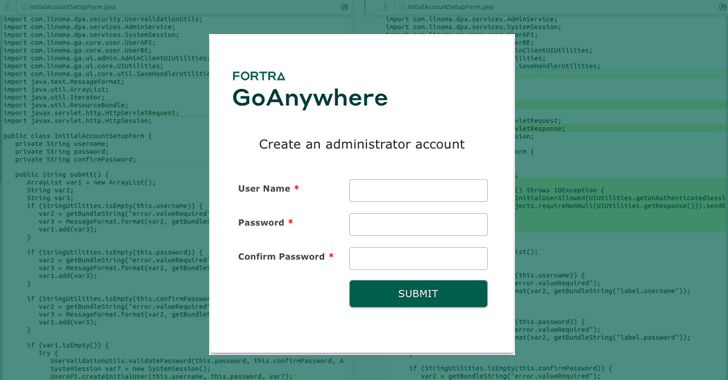
A critical security flaw (CVE-2024-0204) in Fortra’s GoAnywhere MFT software allows unauthorized user to create admin user. Users unable to upgrade to v7.4.1 should delete InitialAccountSetup.xhtml file in non-container deployments. For container-deployed instances, file should be replaced with empty file and restarted. No evidence of active exploitation. (Words: 49)
Key Takeaways from the Meeting Notes:
– A critical security flaw, tracked as CVE-2024-0204, has been disclosed in Fortra’s GoAnywhere Managed File Transfer (MFT) software. It allows an unauthorized user to create an admin user via the administration portal, carrying a CVSS score of 9.8 out of 10.
– Users who cannot upgrade to version 7.4.1 of GoAnywhere MFT can apply temporary workarounds, depending on the deployment type, to mitigate the security issue.
– The flaw was discovered and reported by Mohammed Eldeeb and Islam Elrfai of Cairo-based Spark Engineering Consultants in December 2023.
– Cybersecurity firm Horizon3.ai published a proof-of-concept (PoC) exploit for CVE-2024-0204, highlighting a path traversal weakness in the “/InitialAccountSetup.xhtml” endpoint.
– Although there is no evidence of active exploitation of CVE-2024-0204 in the wild, a similar flaw in the product (CVE-2023-0669) was abused by the Cl0p ransomware group to breach nearly 130 victims last year.
Given the severity of the security flaw and the potential for exploitation, it is crucial for organizations to take immediate action to address this vulnerability in their Fortra’s GoAnywhere MFT software. This may involve applying the recommended workarounds or upgrading to version 7.4.1 to mitigate the risk of unauthorized user creation and potential compromise of sensitive data.