January 24, 2024 at 09:45AM
A critical loophole named Sys:All in Google Kubernetes Engine (GKE) has been discovered by cybersecurity researchers, allowing threat actors with a Google account to take control of GKE clusters. Around 250,000 active GKE clusters are susceptible. Google has taken steps to address the issue in GKE versions 1.28 and later. Orca has advised users to secure their cluster access controls to prevent potential exploitation.
Based on the meeting notes, the key takeaways are:
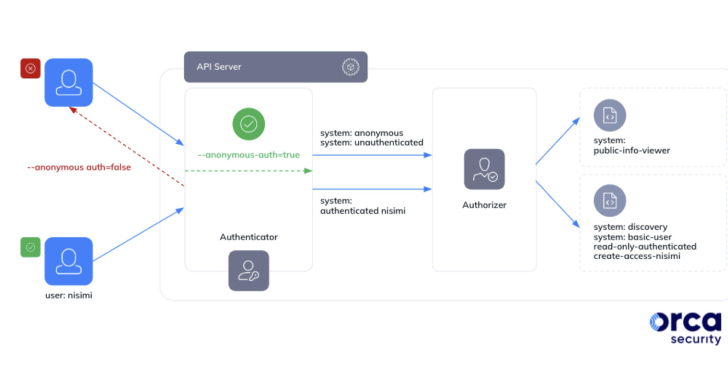
– A critical vulnerability codenamed Sys:All has been identified in Google Kubernetes Engine (GKE), impacting as many as 250,000 active GKE clusters.
– The vulnerability stems from a misconception about the system:authenticated group in GKE, allowing threat actors with a Google account to take control of a Kubernetes cluster and exploit it for various malicious activities.
– Google has taken steps to address the vulnerability in GKE versions 1.28 and later by blocking the binding of the system:authenticated group to the cluster-admin role and providing recommendations for securing cluster access controls.
If you need a more detailed summary or have any specific questions, feel free to ask.