January 25, 2024 at 11:48AM
Over 5,000 unpatched GitLab servers are vulnerable to account takeover due to CVE-2023-7028. The flaw, affecting versions 16.1.0 and onwards, allows send password reset emails to unverified addresses, disclosed by a non-profit group. Patches are available in GitLab versions 16.5.6, 16.6.4, and 16.7.2, with hundreds of vulnerable servers globally. GitLab urges immediate updates as exploitation is a risk.
Key takeaways from the meeting notes are as follows:
1. More than 5,000 GitLab servers are still unpatched against a critical vulnerability (CVE-2023-7028) that allows attackers to exploit the password reset process, potentially leading to account takeover.
2. The flaw was introduced in GitLab 16.1.0, and GitLab has released patches for the bug in versions 16.5.6, 16.6.4, and 16.7.2. These patches were also backported to versions 16.1.6, 16.2.9, 16.3.7, and 16.4.5.
3. Despite warnings from GitLab about the critical severity of the bug and the need for immediate updates, more than 5,000 servers remain unpatched.
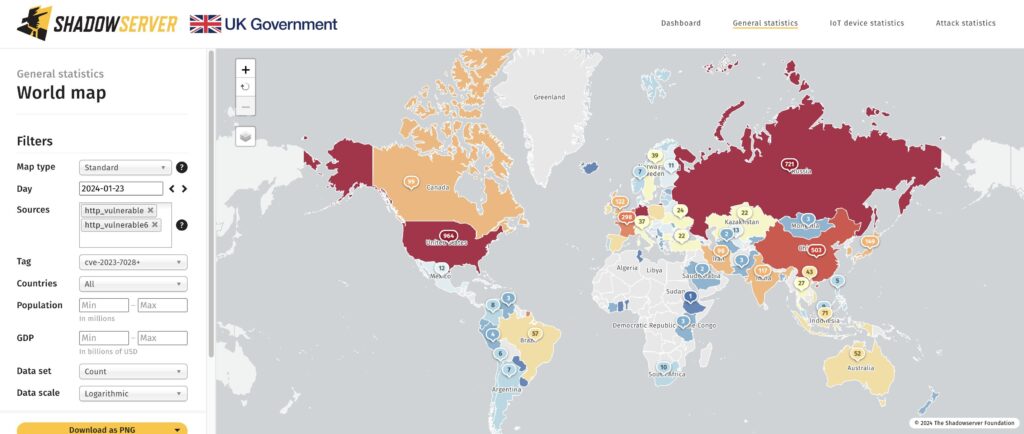
4. The Shadowserver Foundation identified 5,379 vulnerable GitLab instances worldwide, with a significant number located in the US, Germany, Russia, China, France, and the UK.
5. GitLab has not observed the flaw being exploited on its managed platforms but has cautioned self-managed customers to review their logs for signs of exploitation and rotate all credentials if intrusions are detected.
6. GitLab strongly recommends that all installations running affected versions are upgraded to the latest version as soon as possible.
These takeaways provide an overview of the critical vulnerability, the affected GitLab versions, the number of unpatched servers, and recommendations from GitLab.