January 31, 2024 at 07:42AM
The Shadowserver Foundation has identified 45,000 exposed Jenkins instances with a critical vulnerability, potentially being exploited in the wild. Unauthenticated attackers can access limited data from files, while authenticated attackers may obtain full file contents, including sensitive Jenkins secrets. Researchers reported in-the-wild exploitation prior to the public release of the associated proof-of-concept exploit.
It seems that the Shadowserver Foundation has identified 45,000 internet-exposed Jenkins instances that may be affected by a critical vulnerability. There are unconfirmed reports of exploitation in the wild, and the open source CI/CD automation tool has announced patches for CVE-2024-23897, a vulnerability that can allow attackers to read the content of files. This can lead to potential escalation of privileges and arbitrary code execution on the targeted server.
The vulnerability was discovered by the code quality firm Sonar, with technical details published on January 24 and a proof-of-concept (PoC) exploit made public shortly after. Researcher Chaofan Shou reported in-the-wild exploitation on January 25, even before the PoC exploit was published. They observed attacks with different patterns from various sources, with confirmed in-the-wild exploitation and extraction of the exploit from the attack.
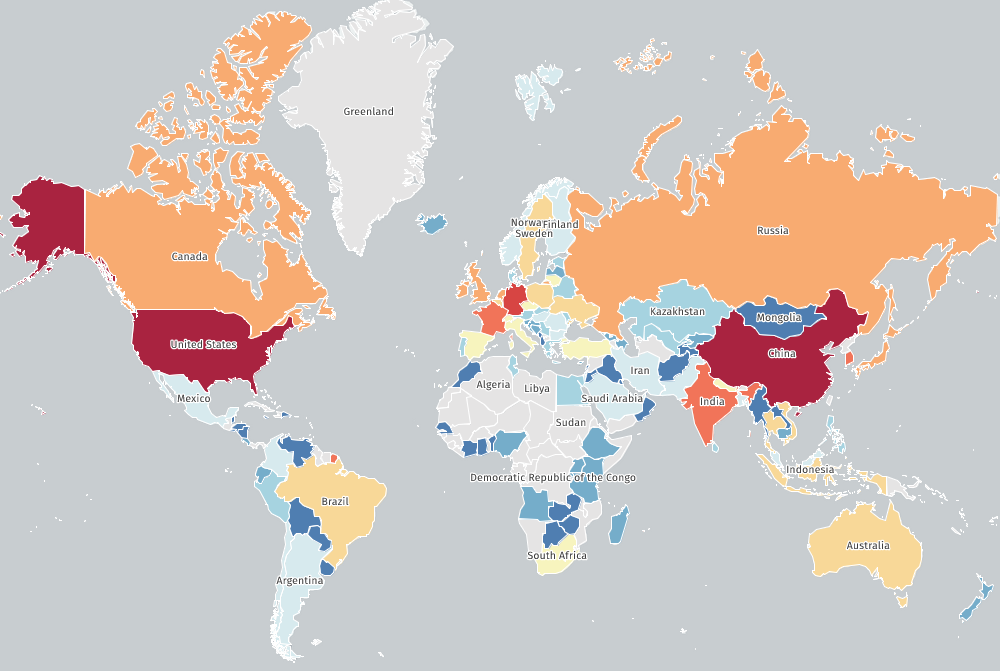
Shadowserver found that a majority of the 45,000 internet-exposed instances are located in the United States and China, each with roughly 11,000 systems, followed by Germany, India, and France. It’s important to note that there may be pending confirmation of in-the-wild exploitation, as some sources have not confirmed these attacks.
Additionally, it’s worth mentioning that the threat intelligence firm GreyNoise currently does not have insights for CVE-2024-23897, but has recently seen a ‘single ping’ targeting an old Jenkins vulnerability disclosed in 2015.