February 28, 2024 at 08:39AM
The U.S. government warns of BlackCat ransomware attacks targeting healthcare, offering a $15 million reward for information. Law enforcement’s takedown of BlackCat suffered a setback, leading to attacks on critical infrastructure organizations. Threat actors leverage security flaws in remote access software, impacting compromised organizations globally. Ransomware groups employ sophisticated tactics, including custom tools and direct network access sales. The release of a Linux-specific ransomware threat source code could lead to increased attacks.
Summary of Meeting Notes:
– The U.S. government has issued a warning regarding the resurgence of BlackCat (ALPHV) ransomware attacks, particularly targeting the healthcare sector. The advisory comes from the FBI, CISA, and HHS.
– The BlackCat ransomware operation suffered a setback last year but has since regained control and continues to target critical infrastructure organizations.
– The government has announced financial rewards up to $15 million for information leading to the identification of key members and affiliates of the BlackCat e-crime group.
– LockBit has also reemerged following disruption efforts by the U.K. National Crime Agency.
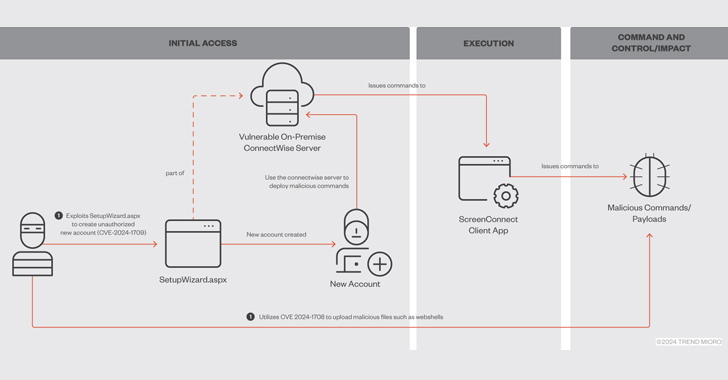
– Threat actors breached Optum’s network by exploiting critical security flaws in ConnectWise’s ScreenConnect software, which have also been leveraged by other ransomware gangs and threat actors to deliver malicious payloads.
– Censys reported over 3,400 exposed potentially vulnerable ScreenConnect hosts online, primarily in the U.S., Canada, the U.K., and other countries.
– Ransomware groups like RansomHouse, Rhysida, and a Phobos variant called Backmydata have been compromising organizations, with RansomHouse developing a custom tool called MrAgent. This tool is designed to automate the deployment of ransomware across large hypervisor environments.
– Some ransomware groups are selling direct network access as a new method of monetization.
– A Linux-specific, C-based ransomware threat known as Kryptina has been released on underground forums, posing a significant risk for the spread and impact of ransomware attacks against Linux systems.
– The meeting notes conclude with an invitation to follow the organization on Twitter and LinkedIn for more exclusive content.
Please let me know if you need further details or clarifications on any specific points from the meeting notes.