February 29, 2024 at 10:42AM
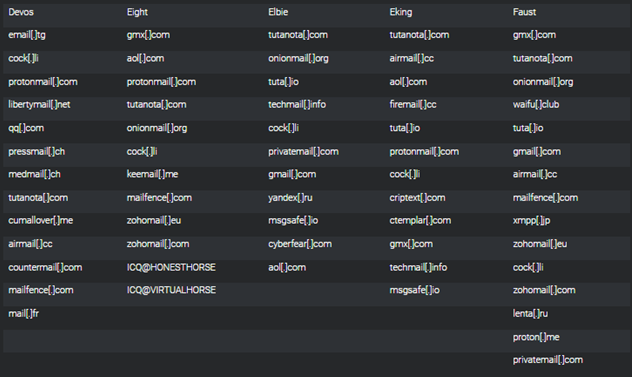
The joint Cybersecurity Advisory (CSA) highlights the Phobos ransomware threat, observed as recently as February 2024. It describes the ransomware’s tactics, techniques, and procedures (TTPs), indicators of compromise (IOCs), and provides recommendations from the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information Sharing and Analysis Center (MS-ISAC). The advisory also emphasizes secure by design and default mitigations, the validation of security controls, and provides additional resources for organizations to enhance their cybersecurity posture.
The meeting notes provide a comprehensive overview of the joint Cybersecurity Advisory (CSA) focusing on the Phobos ransomware variant observed as recently as February 2024. The CSA aims to disseminate known tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) associated with Phobos ransomware to help organizations protect against ransomware incidents.
With a focus on the recommendations in the Mitigations section of the CSA, the key takeaways from the meeting notes are as follows:
– The FBI, CISA, and the MS-ISAC strongly encourage organizations to secure remote access software, implement application controls, and apply log collection best practices, intrusion detection systems, and endpoint detection and response (EDR) solutions to defend against Phobos ransomware and other ransomware incidents.
– It is recommended to align security technologies against the MITRE ATT&CK techniques described in the advisory and to continually test your security program at scale in a production environment to ensure optimal performance against the identified threat behaviors.
Furthermore, the CSA provides a list of mitigations focusing on secure by design and default principles, along with various resources, references, and reporting channels for organizations to refer to when dealing with ransomware incidents.
Overall, the CSA emphasizes the importance of proactive cybersecurity measures to mitigate the likelihood and impact of Phobos ransomware and other ransomware incidents.
If you require any additional information or further clarification on the meeting notes, please feel free to ask.