March 25, 2024 at 06:18AM
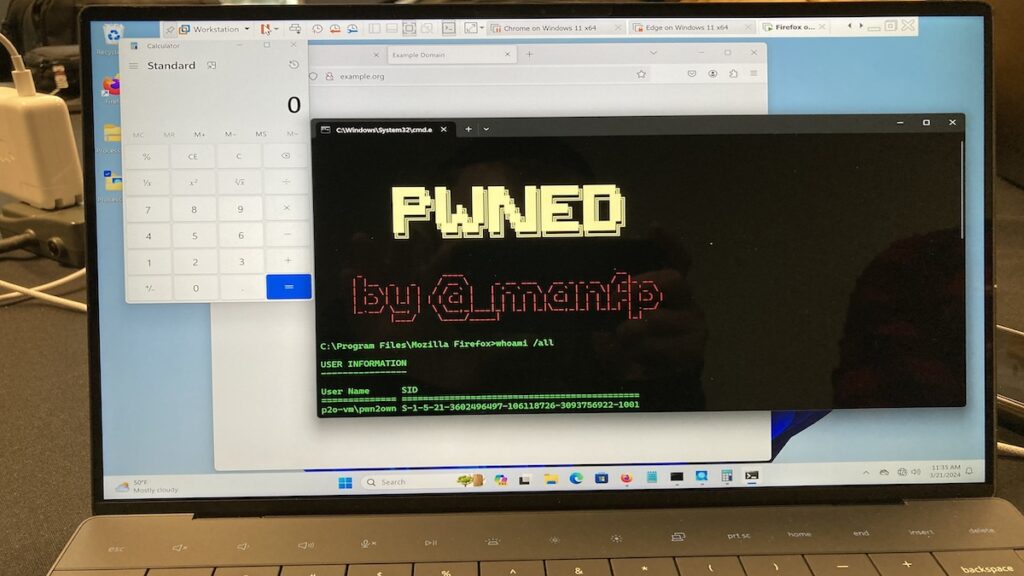
Mozilla has released updates for the Firefox browser to fix two zero-day vulnerabilities that were exploited at the Pwn2Own Vancouver 2024 hacking contest. The first vulnerability allows for bypass of range analysis, while the second issue leads to a sandbox escape. Both vulnerabilities are considered critical and were patched in Firefox 124.0.1 and Firefox ESR 115.9.1.
Based on the meeting notes provided, here are the key takeaways:
1. Mozilla released Firefox browser updates to address two zero-day vulnerabilities exploited at the Pwn2Own Vancouver 2024 hacking contest. The vulnerabilities, discovered by security researcher Manfred Paul, allowed for the execution of code outside the browser’s sandbox.
2. The first vulnerability, tracked as CVE-2024-29943, involves an out-of-bounds access flaw leading to the bypass of range analysis.
3. The second vulnerability, CVE-2024-29944, is a privileged JavaScript execution issue in event handlers, resulting in a sandbox escape. This bug only affects the desktop version of Firefox and cannot be exploited against the mobile app.
4. Both vulnerabilities are categorized as ‘critical severity’ by Mozilla, and patches were released in Firefox 124.0.1 and Firefox ESR 115.9.1.
5. The Zero Day Initiative (ZDI) reported that Manfred Paul used an out-of-bounds write for the remote code execution (RCE) and an exposed dangerous function bug to achieve a sandbox escape in Mozilla Firefox.
6. Manfred Paul was declared the winner of Pwn2Own and received substantial bug bounty rewards for vulnerabilities reported in Firefox, Chrome, Safari, and Edge browsers.
7. Related updates for other browsers include Chrome 123, Firefox 124, Chrome 122, Firefox 123, and Firefox 122, addressing various vulnerabilities.
Let me know if you need more information or if there’s anything else I can assist you with.