April 5, 2024 at 06:33AM
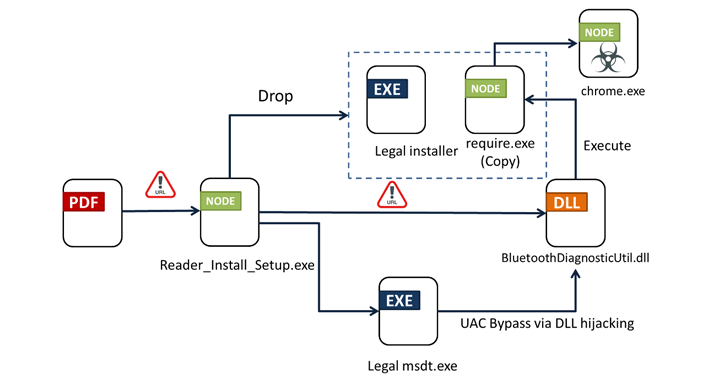
Bogus Adobe Acrobat Reader installers are distributing a new multi-functional malware called Byakugan. The attack begins with a PDF file in Portuguese prompting the victim to download the Reader application. Clicking the link leads to the installation of the malware, which leverages various techniques to deploy its payload and gather system data. The campaign was recently disclosed by security researchers.
Key takeaways from the meeting notes:
– A new multi-functional malware called Byakugan is being distributed through bogus installers for Adobe Acrobat Reader.
– The attack chain leverages techniques like DLL hijacking and Windows User Access Control (UAC) bypass to load and activate the infection sequence.
– Byakugan can gather and exfiltrate system metadata, drop the main module from a different server acting as its command-and-control (C2) server, and perform various malicious activities.
– There is a trend to use both clean and malicious components in malware, making accurate detections more difficult.
– Another campaign was revealed that propagates the Rhadamanthys information stealer under the guise of an installer for groupware, using the indirect syscall technique to hide from security solutions.
– A manipulated version of Notepad++ is being employed to propagate the WikiLoader malware.
For further details and exclusive content, you can follow us on Twitter and LinkedIn.