October 18, 2023 at 08:55AM
Modern enterprises face the challenge of balancing the need for data collaboration and expanded access with the increased risk of cybersecurity threats. Traditional data security measures are insufficient for the data needs of modern enterprises. The CISO Survival Guide emphasizes the importance of data access control and the intersection of data and identity. The ability to see and track data access is crucial for compliance and investigations. Enterprises should focus on improving data collaboration through federated access controls and fine-grained access controls, while also adopting modern practices to stay agile, accessible, and secure in leveraging data for business growth.
Key takeaways from the meeting notes are:
1. Data security in modern enterprises poses both challenges and opportunities. As enterprises seek to derive value from growing data, they must balance data collaboration and access with the increased risk of cybersecurity threats.
2. Traditional approaches to data security, led by CISOs using legacy tools, are insufficient for the needs of modern enterprises. Coarse-grained access controls often impede visibility and hinder effective collaboration.
3. Data access control and data identity are crucial for securing data in the modern enterprise. Identifying groups and individuals with access to specific types of data and tracking data access are key priorities.
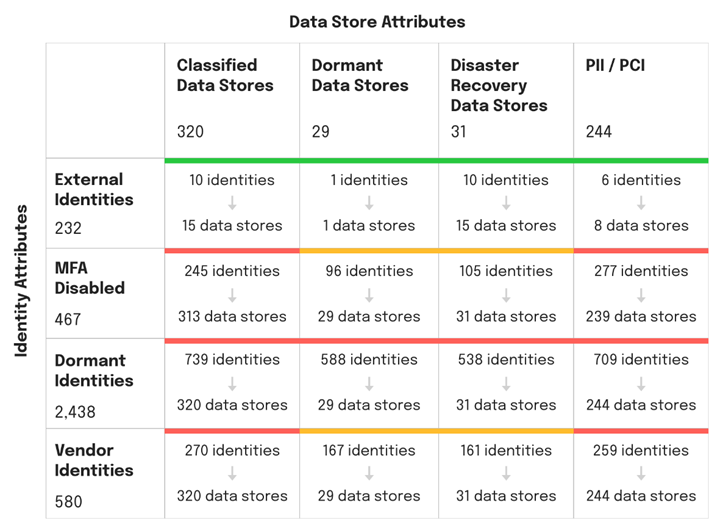
4. Symmetry Systems offers an executive Data Security Scorecard that helps CISOs and compliance teams identify and address over-privileged access to both on-premises and cloud data stores.
5. Improved data collaboration is essential for enterprises. Key concepts include federated data access controls, fine-grained access controls at the row, column, and cell levels, and eliminating the need for data copying by enabling seamless collaboration on data sets.
6. Companies should approach data collaboration at the line-of-business level, gradually unlocking data collaboration in segments of the enterprise. Companies that cling to legacy data security practices may fall behind in agility, accessibility, and security, hindering their ability to leverage data for business growth.