October 18, 2023 at 01:48PM
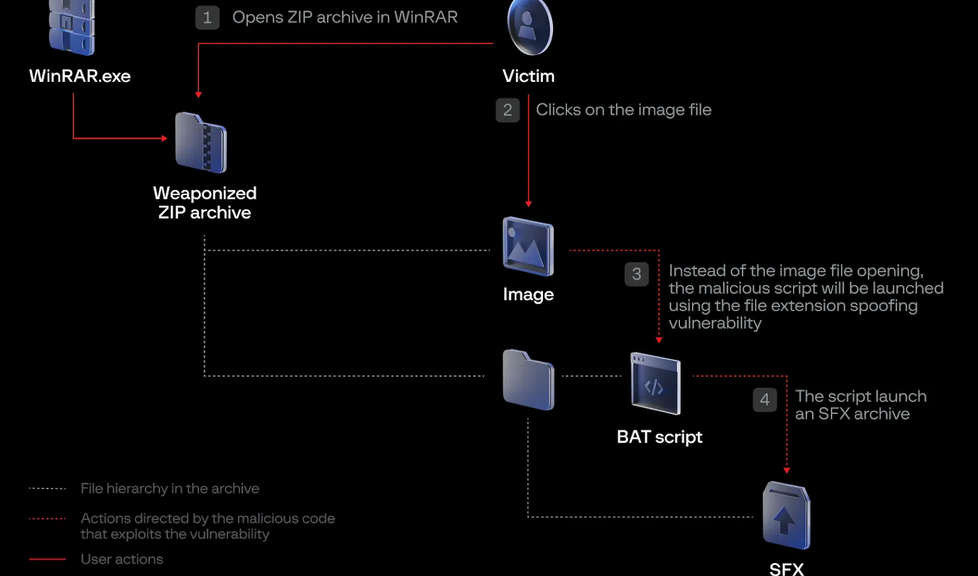
Google’s Threat Analysis Group has found that government-backed hacking groups from Russia and China are still using a security flaw in the WinRAR file archiving utility, despite patches being released three months ago. The vulnerability, which allows attackers to execute code, has been known since at least April and is being actively exploited by cybercriminals. Google warns that the widespread exploitation of the flaw highlights the effectiveness of known vulnerabilities, even with a patch available. WinRAR has been frequently targeted by cybercriminals and advanced threat actors.
During the meeting, it was discussed that government-backed hacking groups from different countries, including Russia and China, continue to exploit a security flaw in the popular WinRAR file archiving utility. The vulnerability, known as CVE-2023-38831, was patched in July after zero-day exploitation was detected. However, malicious actors are still successfully using the exploit more than three months later. The flaw allows attackers to execute arbitrary code when a user attempts to view a benign file within a ZIP archive. The exploit has been known since at least April 2023 and quickly gained the interest of threat actors. Google’s Threat Analysis Group (TAG) has observed the Russia-linked Sandworm and APT28 groups using the exploit to deliver malicious files and infostealers. Additionally, government-backed groups linked to China have launched WinRAR exploits in targeted attacks against users in Papua New Guinea. The widespread exploitation of this vulnerability emphasizes the effectiveness of known vulnerabilities, even with a patch available. It is important for users to stay vigilant and promptly apply security patches to protect against such exploits.