October 18, 2023 at 08:15AM
Attackers in the cybersecurity landscape are constantly searching for vulnerabilities and exploit combinations within organizational environments. Security tools often fail to prioritize threats effectively and provide context on how issues can be leveraged by attackers. Real-life attack path scenarios reveal that 75% of critical assets can be compromised in their current security state, emphasizing the need for effective tools. This article examines seven attack paths encountered by experts, including scenarios involving a financial company, a travel company, a healthcare provider, a global financial institution, a public transportation company, a hospital, and a shipping and logistics company. Remediation strategies involved disabling vulnerable systems, patching, education on security practices, and user removal. The key takeaway is that organizations need tools that offer a contextual understanding of their environments to prioritize necessary remediations effectively.
Based on the meeting notes, here are the key takeaways:
1. Organizations often face challenges in prioritizing threats and understanding how individual issues can be leveraged by attackers.
2. The study conducted by XM Cyber’s Exposure Management Platform revealed that 75% of an organization’s critical assets can be compromised, and 94% can be compromised in just four steps or fewer from the initial breach point.
3. The first real-life attack path scenario involved a large financial company facing a Man-in-the-Middle attack through unsecured DHCP v6 broadcasts. The remediation included disabling DHCPv6, patching vulnerable systems, and educating developers on SSH key security.
4. A large travel company neglected to apply critical patches on a server, potentially compromising critical assets. The solution was to disable the unnecessary server to reduce risk.
5. A large healthcare provider faced an attack path that exploited authenticated users’ group permissions, potentially granting domain admin access. The remediation involved removing permissions to modify paths.
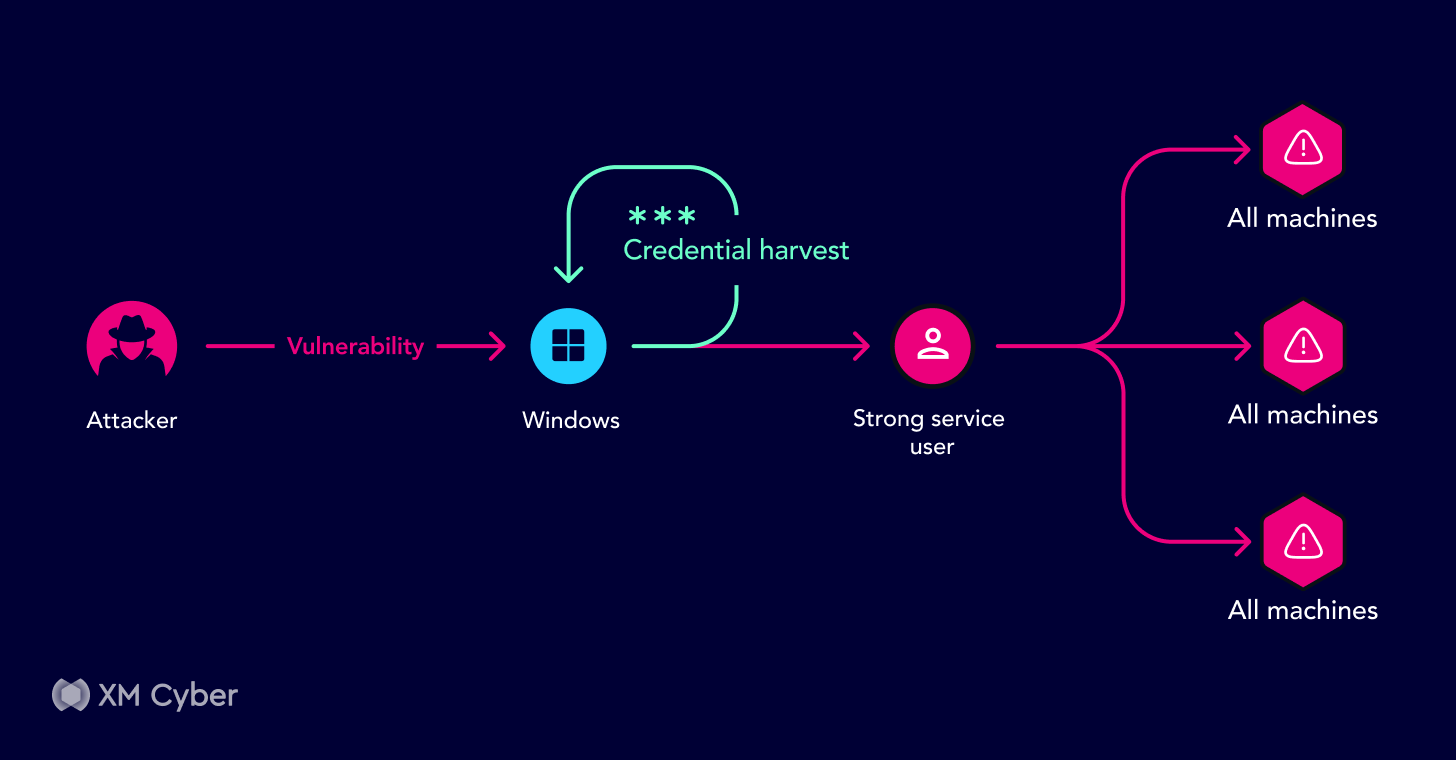
6. A global financial institution experienced a complex attack path involving service accounts, SMB ports, SSH keys, and IAM roles. The remediation required the removal of private SSH keys, resetting IAM role permissions, and user removal.
7. A public transportation company discovered a direct path from a DMZ server to domain compromise, requiring immediate remediation through permissions restriction and user removal.
8. An Active Directory misconfiguration in a hospital allowed any authenticated user to reset passwords, expanding the attack surface. Remediation involved active directory security hardening and a comprehensive remediation plan.
9. A major shipping and logistics company identified an intricate attack path from a workstation machine to Azure, potentially compromising the entire enterprise environment. The remediation included user role adjustments and issue remediation.
The common takeaway from these scenarios is that organizations need the right tools to gain a contextual understanding of their environments. Viewing risks in isolation can create a false sense of security. By understanding how different issues intersect, organizations can prioritize necessary remediations and strengthen their overall security posture.