October 20, 2023 at 10:09AM
A malvertising campaign using Google Ads has been discovered that targets users searching for popular software. The campaign directs users to fake landing pages and distributes malware payloads. The attack filters out bots and unwanted IP addresses, and redirects potential victims to replica websites. The malware establishes a connection to a remote domain and serves further malware. Similar campaigns have also been observed targeting users searching for the KeePass password manager. Malvertising attacks are becoming more sophisticated, combining tactics such as Punycode domain names and rogue Google Ads. Additionally, threat actors are using fake browser updates to propagate malware.
Key Takeaways from Meeting Notes:
– Details have emerged about a malvertising campaign that utilizes Google Ads to redirect users searching for popular software to fake landing pages and distribute malware.
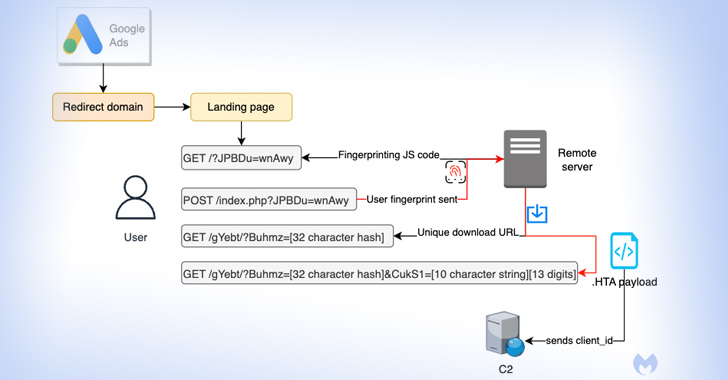
– Malwarebytes discovered the campaign, which is unique in its ability to fingerprint users and distribute time-sensitive payloads.
– The attack targets users searching for Notepad++ and PDF converters by serving bogus ads on the Google search results page.
– If a user is deemed of interest to the threat actor, they are redirected to a replica website advertising the software while silently fingerprinting their system.
– Users who fail the check are directed to the legitimate Notepad++ website, while potential targets are assigned a unique ID for tracking purposes.
– The final-stage malware is an HTA payload that establishes a connection to a remote domain and serves follow-on malware.
– A similar campaign targets users searching for the KeePass password manager with malicious ads that redirect victims to a domain using Punycode.
– Users who land on the decoy site are tricked into downloading a malicious installer that leads to the execution of FakeBat (EugenLoader).
– Threat actors are combining Punycode with rogue Google Ads to conduct homograph attacks and lure victims into installing malware.
– Multiple threat actors are leveraging fake browser update themes to propagate Cobalt Strike, loaders, stealers, and remote access trojans.
– Fake browser updates abuse end-user trust with compromised websites and customized lures to fool users into clicking.