November 1, 2023 at 10:23AM
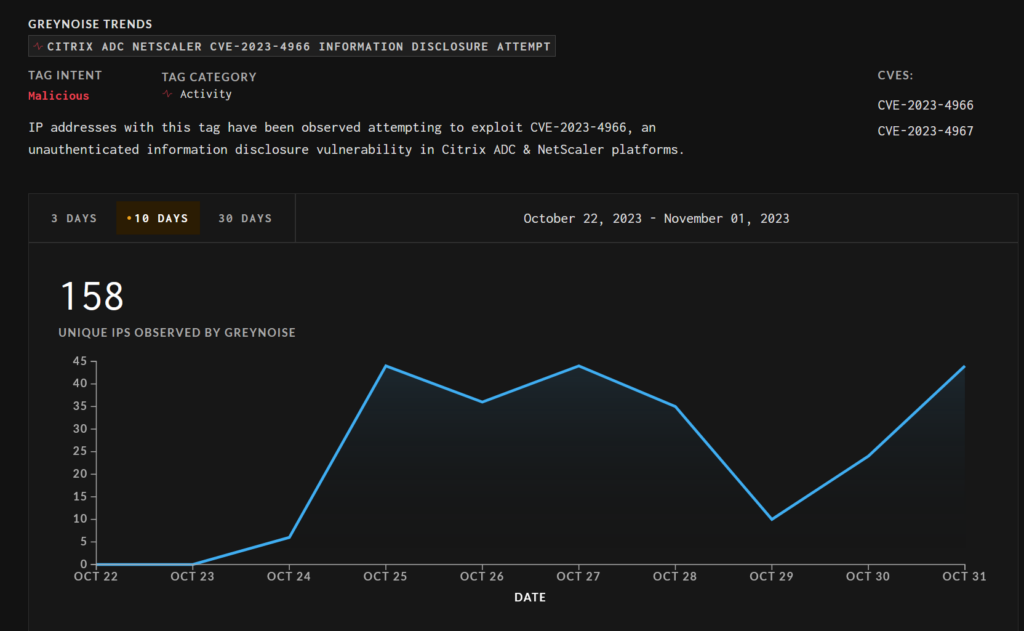
Thousands of Citrix NetScaler ADC and Gateway instances are vulnerable to a critical flaw, dubbed ‘Citrix Bleed’, that allows unauthenticated attackers to leak sensitive information. The vulnerability is actively being exploited by threat actors, including ransomware groups. Citrix has released patches, but roughly half of NetScaler customers have yet to apply them. The cybersecurity firm Mandiant is tracking four threat actors targeting the vulnerability and has provided instructions for identifying evidence of session hijacking.
Meeting Notes Summary:
– There is a critical vulnerability in Citrix NetScaler ADC and Gateway instances, known as ‘Citrix Bleed’ or CVE-2023-4966, which allows unauthenticated attackers to leak sensitive information.
– The flaw has been exploited since August and remains unpatched in thousands of instances.
– Threat actors are actively exploiting the vulnerability to perform session hijacking and bypass authentication.
– Multiple groups, including ransomware groups, are targeting internet-accessible NetScaler ADC and Gateway instances.
– The mass exploitation started around the same time a technical writeup and proof-of-concept exploit for the vulnerability were published.
– Even patched instances are at risk of exploitation as session tokens persist in memory.
– Attackers can gain memory access, extract session cookies, and replay sessions for authentication.
– Roughly half of NetScaler customers have not applied the patches, including organizations in telecommunication, electric, food, and government sectors.
– Organizations should apply available patches, kill active and persistent sessions, and there are no known workarounds or mitigations beyond these steps.
– Multiple threat actors are actively targeting the vulnerability, compromising NetScaler servers, and performing post-exploitation activities.
– They have deployed various tools for reconnaissance, credential theft, persistent access, backdoor, and lateral movement.
– Organizations can use web application firewalls or network appliances to hunt for exploitation attempts.
– Mandiant has published instructions for identifying evidence of session hijacking and indicators-of-compromise (IoCs).
– Attacks have targeted government, legal and professional services, and technology organizations globally.