November 14, 2023 at 06:57AM
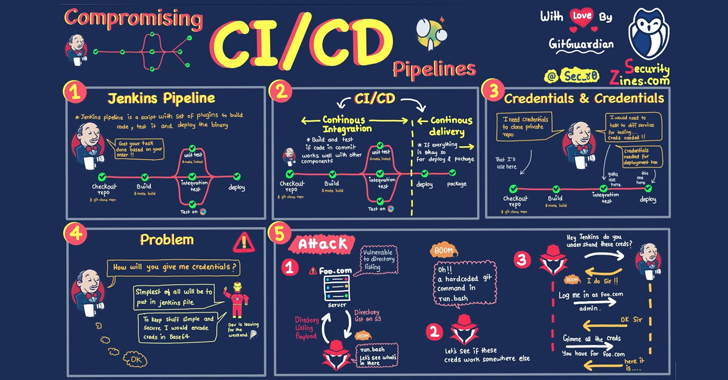
Dependabot, a tool that automates checking and updating outdated dependencies in software projects, has revolutionized software maintenance tasks. However, security firm Checkmarx has warned of malicious actors impersonating Dependabot to deceive developers into accepting unauthorized changes. This incident highlights the vulnerabilities in CI/CD pipelines, which connect external tools and platforms with internal processes, necessitating a focus on pipeline security. Implementing secure-by-design workflows, restricting access, utilizing multi-factor authentication, and safeguarding secrets are some measures to protect CI/CD pipelines and the software supply chain.
Based on the meeting notes, the key takeaways are:
1. Dependabot is a tool that automates the checking and updating of outdated software dependencies in GitHub-hosted projects. It has revolutionized this tedious task and set a new standard for continuous integration providers.
2. There has been a recent incident where malicious actors impersonated Dependabot and tried to deceive developers into accepting changes without careful consideration. This highlights the broader complexities and vulnerabilities inherent in CI/CD pipelines.
3. CI/CD pipelines connect the external world of software development tools and platforms with the internal processes of software creation and deployment. While they provide numerous benefits, they also create potential risks, such as incorporating malicious code or exposing credentials.
4. CI/CD breaches frequently occur due to compromised secrets or targeted attacks on developers. It’s crucial to recognize that the issue lies in the lack of inherent security in CI/CD pipelines.
5. CI/CD platforms often prioritize ease of use over robust security measures, resulting in a lack of default safeguards to prevent potential issues. Developers should take additional measures to harden their pipelines against attacks.
6. Best practices for securing CI/CD pipelines include restricting access and minimizing privileges, enforcing multi-factor authentication, utilizing OpenID Connect, using pre-reviewed software dependencies, securing runtime secrets, implementing advanced defense systems, and leveraging enterprise-scale solutions.
7. Organizations can comprehensively safeguard their CI/CD pipelines and software supply chain by combining these strategies.
For more exclusive content and updates, you can follow the provider of this article on Twitter and LinkedIn.