November 17, 2023 at 08:48AM
Threat actors are using manipulated search results and bogus Google ads to trick users into downloading malware instead of legitimate software, such as WinSCP. The attack involves redirecting users to a compromised WordPress website, then an attacker-controlled phishing site, and finally to a fake WinSCP website where they unknowingly download the malware. The attackers are leveraging Google’s Dynamic Search Ads to serve the malicious ads. The payload includes a ZIP file with a setup executable that employs DLL side-loading and Python scripts to execute malicious behavior. The targets appear to be limited to those seeking WinSCP software, and the attack mainly targets users in the United States. This is not the first time Google’s Dynamic Search Ads have been abused for malware distribution. Malvertising has become increasingly popular among cybercriminals in recent years.
Key Takeaways:
– Threat actors are using manipulated search results and bogus Google ads to trick users into downloading malware instead of legitimate software like WinSCP.
– The ongoing activity is being tracked by cybersecurity company Securonix under the name SEO#LURKER.
– The malicious ads direct users to a compromised WordPress website, which then redirects them to an attacker-controlled phishing site.
– The attackers leverage Google’s Dynamic Search Ads to serve the malicious ads and take victims to the infected site.
– The ultimate goal is to entice users into visiting a fake WinSCP website, winccp[.]net, and downloading the malware.
– If the referrer is incorrect, users are redirected to the Rick Astley YouTube video.
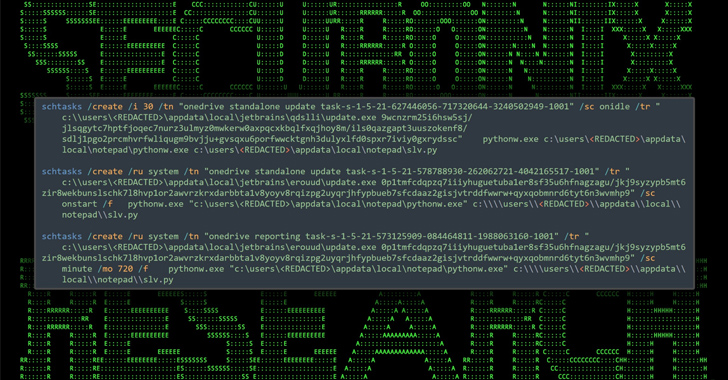
– The final payload is a ZIP file labeled “WinSCP_v.6.1.zip” that contains a setup executable and a DLL file named python311.dll.
– The DLL file downloads and executes a legitimate WinSCP installer while also activating malicious Python scripts for further instructions and persistence.
– The attack primarily targets individuals seeking WinSCP software, with geoblocking suggesting victims are primarily in the U.S.
– Google’s Dynamic Search Ads have been previously abused to distribute malware, such as a campaign targeting users searching for PyCharm.
– Malvertising has become popular among cybercriminals for launching malware campaigns, including credit card skimming attacks on e-commerce websites.