December 29, 2023 at 06:54AM
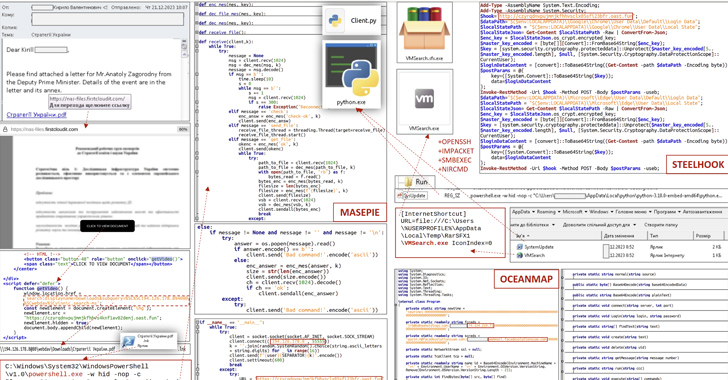
Ukraine’s CERT-UA has warned of a new phishing campaign by the Russia-linked APT28 group targeting government entities through email messages, deploying malware such as OCEANMAP, MASEPIE, and STEELHOOK to harvest sensitive information. The attacks utilize various tools, including the Python-based MASEPIE and the C#-based OCEANMAP, with communications employing encrypted channels. Previous APT28 activities have utilized lures related to the Israel-Hamas war and exploited a critical security flaw in Outlook email service.
Key takeaways from the meeting notes on Newsroom Email Security/Malware:
– The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new phishing campaign by the Russia-linked APT28 group, deploying previously undocumented malware such as OCEANMAP, MASEPIE, and STEELHOOK to harvest sensitive information.
– The phishing campaign targets government entities with deceptive email messages urging recipients to click on a link to view a document, which in reality redirects to malicious web resources.
– The malware MASEPIE is Python-based and capable of downloading/uploading files, executing commands, and communicating with a command-and-control (C2) server over an encrypted channel using the TCP protocol.
– The PowerShell script STEELHOOK is capable of harvesting web browser data and exporting it to an actor-controlled server in Base64-encoded format.
– A C#-based backdoor called OCEANMAP is designed to execute commands using cmd.exe, using the IMAP protocol as a control channel and achieving persistence by creating a URL file in the Windows Startup folder.
– APT28 has been attributed to the exploitation of a now-patched critical security flaw in Outlook email service, gaining unauthorized access to victims’ accounts within Exchange servers.
– APT28 leveraged lures related to the ongoing Israel-Hamas war and a critical security flaw in Outlook email service to facilitate the delivery of a custom backdoor called HeadLace.
– Further reconnaissance and lateral movement activities are carried out within an hour of the initial compromise by taking advantage of tools like Impacket and SMBExec, according to the CERT-UA.
Please let me know if you need further details.