January 1, 2024 at 02:00AM
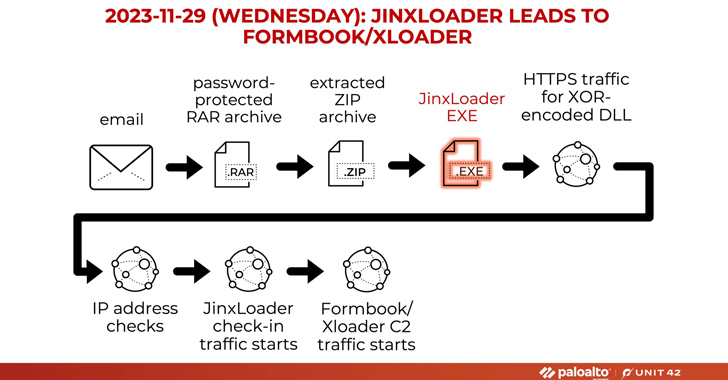
JinxLoader, a new Go-based malware loader, has been identified as a method used by threat actors to deliver next-stage payloads such as Formbook and XLoader. Cybersecurity firms highlighted its use in multi-step attack sequences via phishing emails impersonating Abu Dhabi National Oil Company, leading to a surge in infections and the release of new stealer families on the dark web.
Based on the meeting notes, the key takeaways are:
1. New malware loader called JinxLoader, used to deliver next-stage payloads such as Formbook and XLoader, discovered by cybersecurity firms Palo Alto Networks Unit 42 and Symantec.
2. JinxLoader primarily functions as a loader for malware and was first advertised on hackforums[.]net in April 2023 for a monthly, yearly, or lifetime fee.
3. The attacks involving JinxLoader begin with phishing emails impersonating Abu Dhabi National Oil Company (ADNOC) and lead to the deployment of Formbook or XLoader.
4. ESET reported a spike in infections, with a new novice loader malware family called Rugmi, and a surge in campaigns distributing DarkGate, PikaBot, and IDAT Loader by threat actors known as TA544.
5. Updated version of Meduza Stealer (version 2.2) released on the dark web with expanded support for browser-based cryptocurrency wallets and an improved credit card (CC) grabber.
6. Discovery of a new stealer family called Vortex Stealer capable of exfiltrating browser data, Discord tokens, Telegram sessions, system information, and files less than 2 MB in size, with capabilities to archive and upload stolen information and post it onto Discord and Telegram.
Feel free to reach out if you need further assistance or additional details.