January 4, 2024 at 04:06AM
The UAC-0050 threat actor is using phishing attacks to distribute the Remcos RAT, employing new tactics to avoid detection by security software. Uptycs researchers highlight the group’s use of a pipe method for interprocess communication, demonstrating advanced adaptability. The group has a history of targeting Ukrainian and Polish entities through social engineering campaigns.
Key Takeaways from the Meeting Notes:
1. Threat actor UAC-0050 is using phishing attacks to distribute the notorious Remcos RAT, employing new strategies to evade security software detection.
2. UAC-0050 has a history of targeting Ukrainian and Polish entities through social engineering campaigns impersonating legitimate organizations.
3. The group has integrated a pipe method for interprocess communication, showcasing advanced adaptability, and previously utilized phishing campaigns to deliver Remcos RAT.
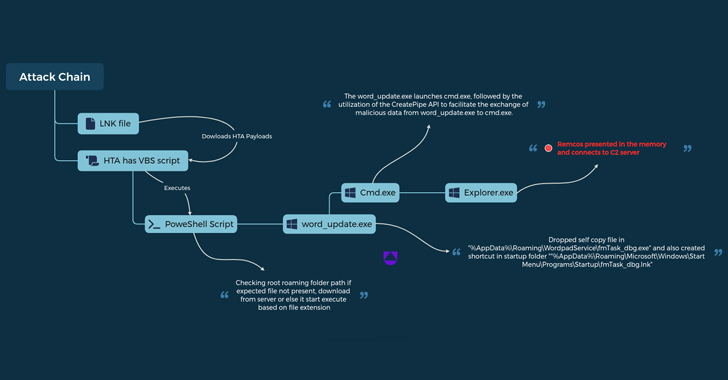
4. The Uptycs analysis, based on a discovered LNK file, suggests that the group targeted Ukrainian military personnel with phishing emails claiming to advertise consultancy roles with the Israel Defense Forces (IDF).
5. The analysis also indicates the use of PowerShell scripts to download and execute files from a remote server, ultimately leading to the deployment of Remcos RAT (version 4.9.2 Pro).
6. The use of unnamed pipes within the Windows operating system provides a covert channel for data transfer, evading detection by Endpoint Detection and Response (EDR) and antivirus systems.
These notes highlight the advanced techniques employed by UAC-0050 and the ongoing threat posed by their sophisticated evasion tactics.