January 23, 2024 at 01:05PM
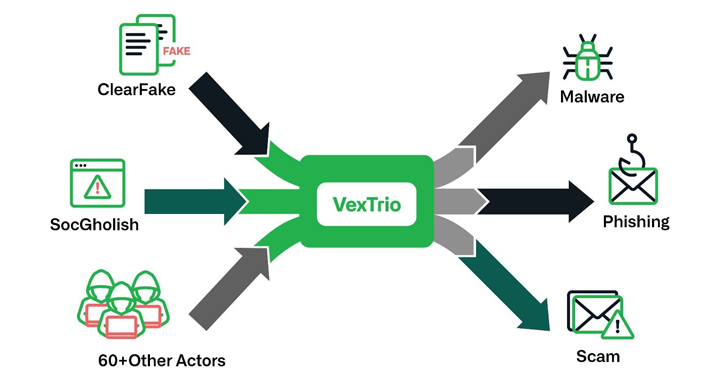
New findings from Infoblox reveal a massive “criminal affiliate program” involving threat actors like ClearFake, SocGholish, and VexTrio. VexTrio, active since 2017, operates a network of over 70,000 domains and brokers traffic for 60 affiliates. It uses DNS and HTTP-based traffic distribution systems to propagate scams, riskware, and more. The entangled and resilient nature of its affiliate network makes attribution challenging and allows it to flourish undetected.
The meeting notes provide detailed information about the activities and connections of VexTrio, a malicious actor operating a large affiliate program in the cybercrime industry. VexTrio has been active since at least 2017, and its operations include distributing malware, brokering traffic for affiliates, and leveraging the Domain Name System (DNS) protocol to redirect visitors to illegitimate content.
Key points to highlight from the meeting notes include VexTrio’s estimated network of over 70,000 known domains, its unique affiliate program structure, and the use of traffic distribution systems (TDS) to route site visitors to malicious content. It’s also important to note VexTrio’s partnerships with other threat actors like ClearFake and SocGholish, as well as its involvement in carrying out its own cyber campaigns and abusing referral programs.
Overall, the meeting notes underscore the complexity and resilience of VexTrio’s operations, making precise classification and attribution challenging for the security industry. It’s clear that VexTrio presents a significant and ongoing threat to cybersecurity.
Let me know if you need any further information or if there are specific takeaways you’d like to emphasize.