February 18, 2024 at 11:57PM
Charming Kitten, an Iranian-origin threat actor also known as APT35, has been linked to new attacks aimed at Middle East policy experts using a new backdoor called BASICSTAR through a fake webinar portal. The group, affiliated with Iran’s Revolutionary Guard Corps, uses a range of social engineering tactics, including phishing and posing as legitimate organizations, to deploy malware and conduct surveillance on their targets. These activities are part of a larger scheme involving a network of contracting companies that export surveillance and offensive technologies to countries in the region.
Based on the meeting notes, the key takeaways are:
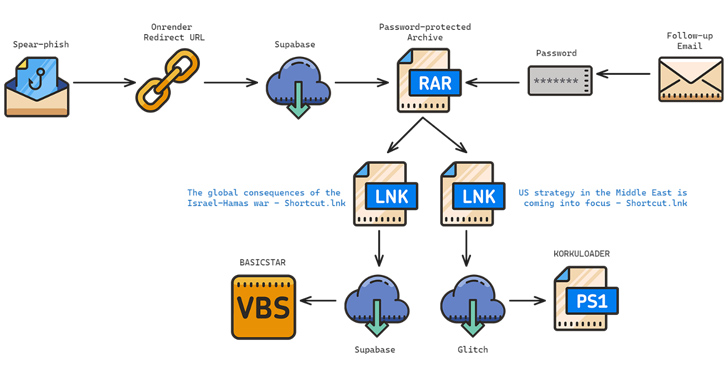
1. Charming Kitten, an Iranian-origin threat actor, has been linked to a new set of attacks targeting Middle East policy experts using a new backdoor called BASICSTAR through a fake webinar portal. The group has a history of employing social engineering tactics to target think tanks, NGOs, and journalists.
2. The adversary has deployed various malware such as MischiefTut, MediaPl, PowerLess, BellaCiao, POWERSTAR, and NokNok to harvest sensitive information from compromised hosts. They have also engaged in phishing attacks posing as the Rasanah International Institute for Iranian Studies (IIIS) and use compromised email accounts for impersonation.
3. The attack chains use RAR archives containing LNK files to distribute malware, with specific backdoors targeted based on the operating system of the victim’s machine (POWERLESS for Windows victims and NokNok for Apple macOS victims).
4. Recorded Future uncovered IRGC’s targeting of Western countries using a network of contracting companies specializing in surveillance and offensive technologies, with close associations to the IRGC and some representatives of sanctioned entities.
These takeaways highlight the persistence and evolving tactics of Charming Kitten and its affiliations with Iranian contracting companies and the IRGC in conducting cyber espionage activities.