February 20, 2024 at 06:27AM
North Korean-sponsored threat actors are conducting cyber espionage targeting the defense sector worldwide. The Lazarus Group is blamed for using social engineering to infiltrate the defense sector through a long-standing operation called Dream Job. Another incident involved an intrusion into a defense research center, executed by a North Korea-based threat actor using a software supply chain attack. This demonstrates the group’s ability to adapt its tactics in response to law enforcement actions.
Key Takeaways from the Meeting Notes:
– North Korean state-sponsored threat actors are conducting cyber espionage targeting the defense sector worldwide, aiming to plunder advanced defense technologies such as ballistic missiles, reconnaissance satellites, and submarines.
– The Lazarus Group has been blamed for using social engineering tactics to infiltrate the defense sector through a campaign called Dream Job, which involves creating fake profiles or compromising legitimate ones on platforms like LinkedIn to approach targets and distribute malware-laden job offer documents.
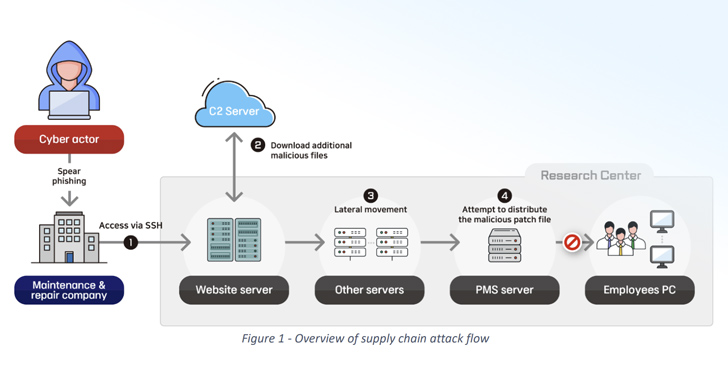
– Another attack involved a software supply chain attack against a web server maintenance company, leading to the theft of account credentials and remote control malware deployment in a defense research center.
– The BfV and NIS highlighted the manipulation of trustful relationships between entities, indicating that threat actors took advantage of vendors to gain access to their intended targets.
– The Lazarus Group has adapted its money laundering tactics, switching to the YoMix bitcoin mixer after the shutdown of Sinbad.
– The malicious activities are attributed to various North Korean hacking units under the Lazarus umbrella, which engage in a range of operations including cyber espionage, cryptocurrency thefts, ransomware, and supply chain attacks.
Overall, the meeting notes outline a significant cyber threat posed by North Korean state-sponsored actors targeting the defense sector and illustrate the evolving tactics used by these threat actors in their operations.