April 5, 2024 at 10:39AM
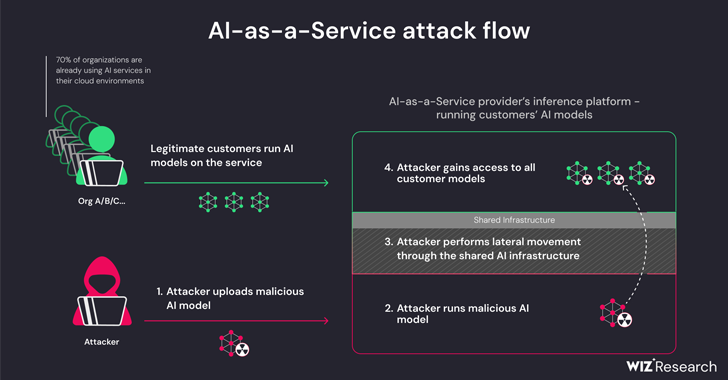
New research has revealed that AI-as-a-service providers, like Hugging Face, are vulnerable to threats allowing attackers to gain access to private AI models and apps. The findings highlight the risk of supply chain attacks on machine learning pipelines. Recommendations include using trusted AI models, enabling multi-factor authentication, and avoiding pickle files in production.
The meeting notes provide a comprehensive overview of the potential risks associated with artificial intelligence (AI) systems and AI-as-a-service providers, particularly in the context of supply chain attacks. The notes highlight the vulnerabilities in AI-as-a-service infrastructure, including the ability for threat actors to escalate privileges, access sensitive information, and compromise the entire service.
The research findings emphasize the importance of exercising caution when utilizing untrusted AI models, especially those based on “Pickle” format, and the need for sandboxed environments for running such models. Additionally, the notes underscore the significance of implementing security measures such as enabling multi-factor authentication (MFA) and avoiding the use of pickle files in production environments.
Furthermore, the meeting notes address the potential risks associated with generative AI models, including the distribution of malicious code packages. It also mentions a new method called “many-shot jailbreaking” that can bypass safety protections built into large language models (LLMs), posing potential risks stemming from vulnerabilities to jailbreaks that exploit the longer context window.
The notes also feature a call to action for individuals interested in reading more exclusive content by encouraging them to follow the organization on Twitter and LinkedIn.
Overall, a key takeaway from the meeting notes is the critical importance of implementing robust security measures and exercising caution when utilizing AI models, especially within the context of AI-as-a-service providers and generative AI models.
Please let me know if you need further information or analysis on any specific aspect of the meeting notes.