April 17, 2024 at 07:12AM
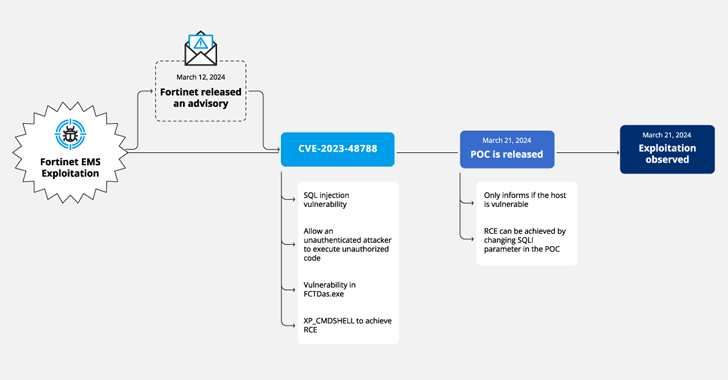
Cybersecurity researchers have uncovered a new campaign exploiting a vulnerability in Fortinet FortiClient EMS devices, allowing unauthorized code execution. The campaign, tracked by Forescout as Connect:fun, utilizes ScreenConnect and Metasploit Powerfun. Organizations are urged to patch the CVE-2023-48788 vulnerability, monitor for suspicious activity, and use a web application firewall for protection.
Key Takeaways from the meeting notes:
1. A new cybersecurity campaign is exploiting a security flaw in Fortinet FortiClient EMS devices to deliver ScreenConnect and Metasploit Powerfun payloads.
2. The campaign involves the exploitation of CVE-2023-48788, a critical SQL injection flaw.
3. The activity is being tracked by cybersecurity firm Forescout under the codename Connect:fun.
4. The campaign targeted an unnamed media company with a vulnerable FortiClient EMS device.
5. The threat actor behind the campaign appears to have been active since at least 2022 and has been using Vietnamese and German languages in their infrastructure.
6. The attack shares tactical and infrastructure overlaps with other incidents involving the abuse of CVE-2023-48788.
7. Organizations are advised to apply patches provided by Fortinet, monitor for suspicious traffic, and use a web application firewall (WAF) to block potentially malicious requests.
These are the key takeaways from the meeting notes. Let me know if you need further assistance or information.