April 24, 2024 at 07:06AM
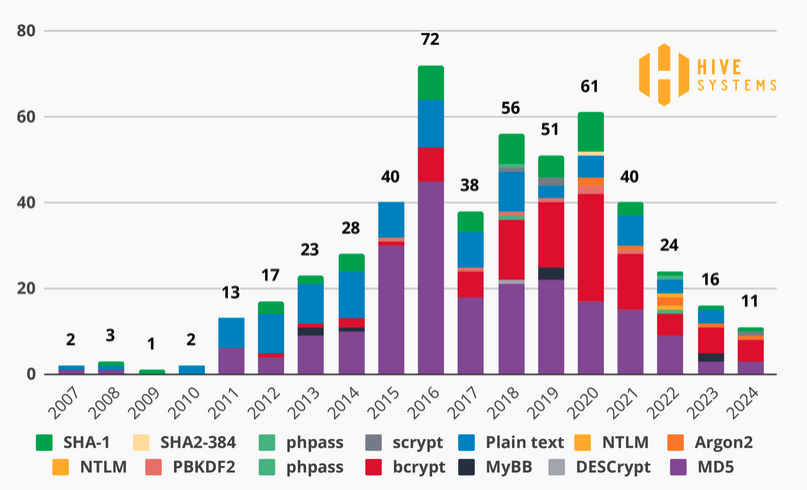
Hive Systems analyzed password cracking through brute-force attacks, shifting from MD5 to Bcrypt. With a dozen NVIDIA GeForce RTX 4090 GPUs, they found that Bcrypt significantly delays cracking times, making strong passwords more secure. However, non-randomly generated passwords can still be breached quickly due to predictability. Hive’s study is based on hash-associated passwords.
The meeting notes from Hive Systems provide key insights into the increasing vulnerability of password security and the importance of using strong, unique passwords to protect sensitive information. The firm’s annual analysis has shifted to testing against Bcrypt password hashes, revealing that passwords under seven characters can be cracked within hours using brute force attacks. Furthermore, the study demonstrates that weak and non-randomly generated passwords are more easily cracked, highlighting the need for strong, randomized passwords to enhance security. Additionally, the notes suggest that strong passwords, particularly those exceeding eight characters and containing a mix of numbers, upper and lower case letters, and symbols, significantly increase the time required for brute force attacks to crack them, ranging from months to years if protected with Bcrypt. This information serves as a valuable reference point for organizations looking to enhance their password security measures.