May 2, 2024 at 08:09AM
GitLab’s email verification vulnerability, tracked as CVE-2023-7028 and with a severity score of 10/10, allowed for password hijacking. GitLab has patched this issue in versions 16.5.6, 16.6.4, and 16.7.2. CISA warns of active exploitation and federal agencies must address vulnerable instances by May 22 under BOD 22-01. All organizations should apply available patches.
Based on the meeting notes, the key takeaways are:
1. GitLab’s email verification process vulnerability (tracked as CVE-2023-7028 with a CVSS score of 10/10) was exploited, potentially leading to password hijacking.
2. GitLab patched the security defect in January 2024 for affected versions 16.1 to 16.7.1, with fixes included in versions 16.5.6, 16.6.4, and 16.7.2, and backported to versions 16.1.6, 16.2.9, 16.3.7, and 16.4.5.
3. CISA added the vulnerability to its Known Exploited Vulnerabilities (KEV) Catalog with evidence of active exploitation.
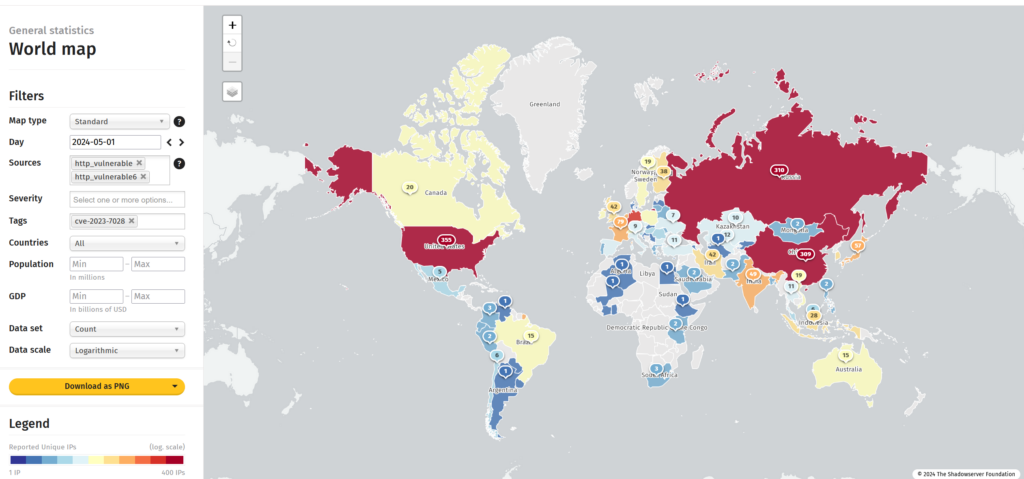
4. The Shadowserver Foundation reported that over 5,300 internet-accessible GitLab servers initially had not been patched, but the number dropped to around 1,400 as of May 1, according to new data.
5. Federal agencies must identify vulnerable GitLab instances in their environments and apply available patches by May 22 as per Binding Operational Directive (BOD) 22-01. However, all organizations are advised to apply patches and mitigations as well.
6. It is crucial for all organizations to stay informed about such vulnerabilities and apply relevant patches and mitigations promptly.