May 6, 2024 at 10:54AM
A critical unpatched security flaw in the Tinyproxy service impacts more than half of the 90,310 exposed hosts, making them vulnerable to remote code execution. The vulnerability, with a CVSS score of 9.8, affects versions 1.10.0 and 1.11.1 and is being actively exploited. Users are urged to update to the latest version and avoid exposing the service to the public internet.
Key takeaways from the meeting notes on Newsroom Vulnerability / Server Security:
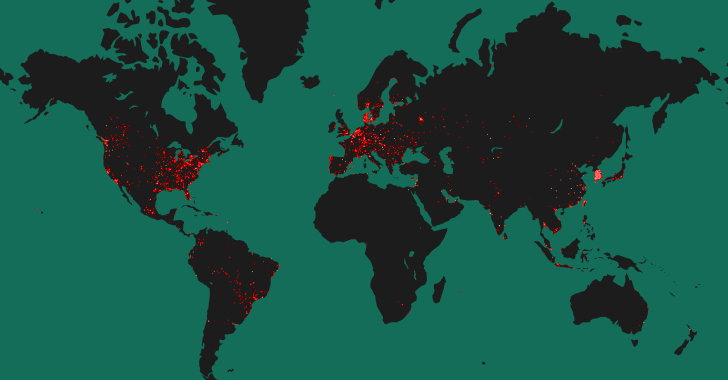
– Over 50% of 90,310 hosts are found exposing a vulnerable version of Tinyproxy service on the internet, posing a significant security risk.
– The vulnerability, tracked as CVE-2023-49606, has a high CVSS score of 9.8 and can lead to remote code execution through a specially crafted HTTP header.
– The majority of the publicly-accessible vulnerable hosts are located in the U.S., South Korea, China, France, and Germany.
– Talos reported the issue in December 2023 and released a proof-of-concept (PoC) for the flaw.
– The maintainers of Tinyproxy have acknowledged the issue and advised users to update to the latest version when available and not expose the service to the public internet.
For more exclusive content, follow us on Twitter and LinkedIn.