July 8, 2024 at 09:29PM
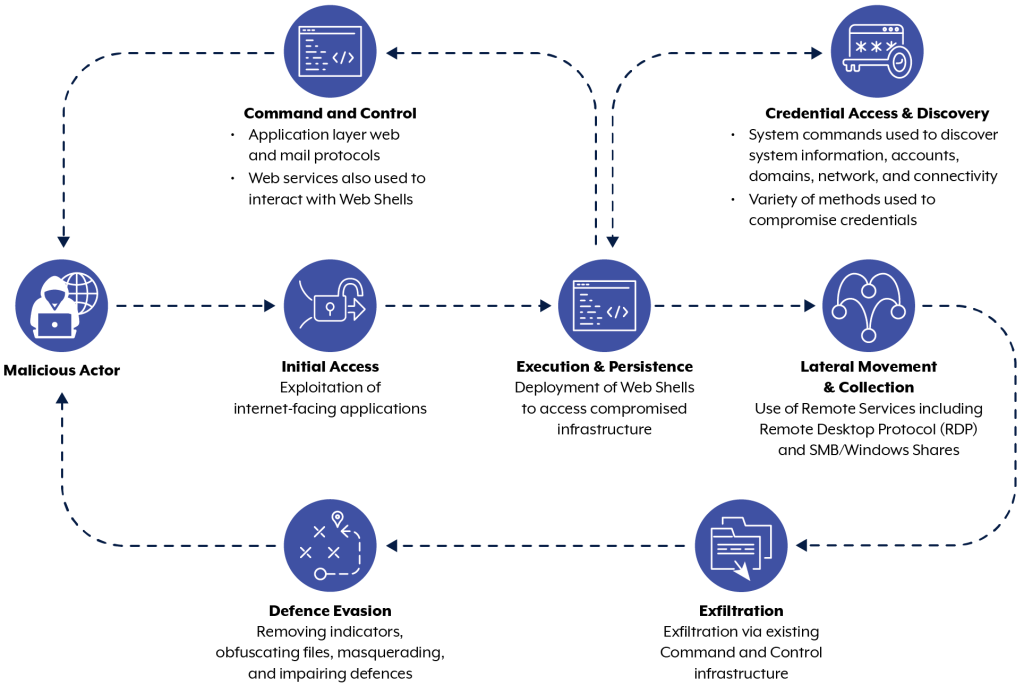
The Australian Signals Directorate, in collaboration with several international security agencies, has issued an advisory outlining the threat posed by a People’s Republic of China state-sponsored cyber group, particularly their targeting of Australian networks. The group, known as APT40, has been reported to conduct malicious cyber operations for the PRC Ministry of State Security, and they have been observed targeting various countries, including Australia and the United States. APT40 is known to use sophisticated techniques such as exploiting vulnerable, public-facing infrastructure and using web shells for persistence. They have also been observed rapidly exploiting newly public vulnerabilities in widely used software. The advisory includes summaries of significant case studies of APT40’s techniques in action against victim networks, as well as recommendations for detection and mitigation strategies. Additionally, the report provides specific reporting and incident response contact information for Australian, Canadian, New Zealand, United Kingdom, and U.S. organizations.
For any further details, please refer to the original document.
Based on the provided meeting notes, the key takeaways are as follows:
1. A state-sponsored Chinese cyber group, referred to as APT40, poses a significant threat to the cybersecurity of multiple countries, including Australia, the United States, and others.
2. APT40 has targeted organizations in various countries, including Australia and the United States, using a variety of techniques and tools to compromise networks and exfiltrate sensitive data.
3. The group demonstrates the capability to rapidly exploit new vulnerabilities in widely used software such as Log4J, Atlassian Confluence, and Microsoft Exchange, indicating a high level of sophistication and adaptability.
4. APT40 regularly uses techniques to establish persistence on victim networks, such as web shells and exploiting network vulnerabilities.
5. The group has also demonstrated the ability to compromise and maintain access to critical infrastructure, including small-office/home-office (SOHO) devices, as operational infrastructure for their operations.
6. The meeting notes provide detailed case studies of two instances where APT40 successfully compromised and exfiltrated data from victim networks, showcasing their tactics, techniques, and procedures (TTPs) employed during such operations.
7. The meeting notes include specific file information related to the malicious files identified and shared by ASD’s ACSC during their investigations.
8. Mitigation recommendations and strategies are provided, including logging, patch management, network segmentation, and other defense and detection mechanisms to combat the identified TTPs employed by APT40.
9. Parties from Australian, Canadian, New Zealand, the United Kingdom, and the United States are encouraged to report cybersecurity incidents and access further support for addressing potential threats.
It’s clear that the identified threat from APT40 is significant, requiring coordinated efforts and a robust cybersecurity posture to detect and mitigate their activities effectively.