October 15, 2024 at 08:10AM
Organizations increasingly rely on digital technologies, making identity the key security perimeter. Despite adopting security measures like MFA and single sign-on, many accounts remain vulnerable to attacks. Research indicates significant gaps in MFA usage and password security, with high risks of credential stuffing and phishing due to weak practices.
### Meeting Takeaways:
1. **Identity as the Security Perimeter**: With the rise of cloud services and remote work, identity management is critical for organizations to authenticate, authorize, and manage users, applications, and devices.
2. **Investment in Identity Technologies**: Organizations must invest in robust identity solutions, including:
– Single Sign-On (SSO)
– Multifactor Authentication (MFA)
– Continuous Monitoring
– Identity Access Management
3. **Vulnerability to Identity-Based Attacks**: Many organizations face significant risks from identity-based attacks, such as credential stuffing, brute-force attacks, and phishing.
4. **Research Findings from Push Security**:
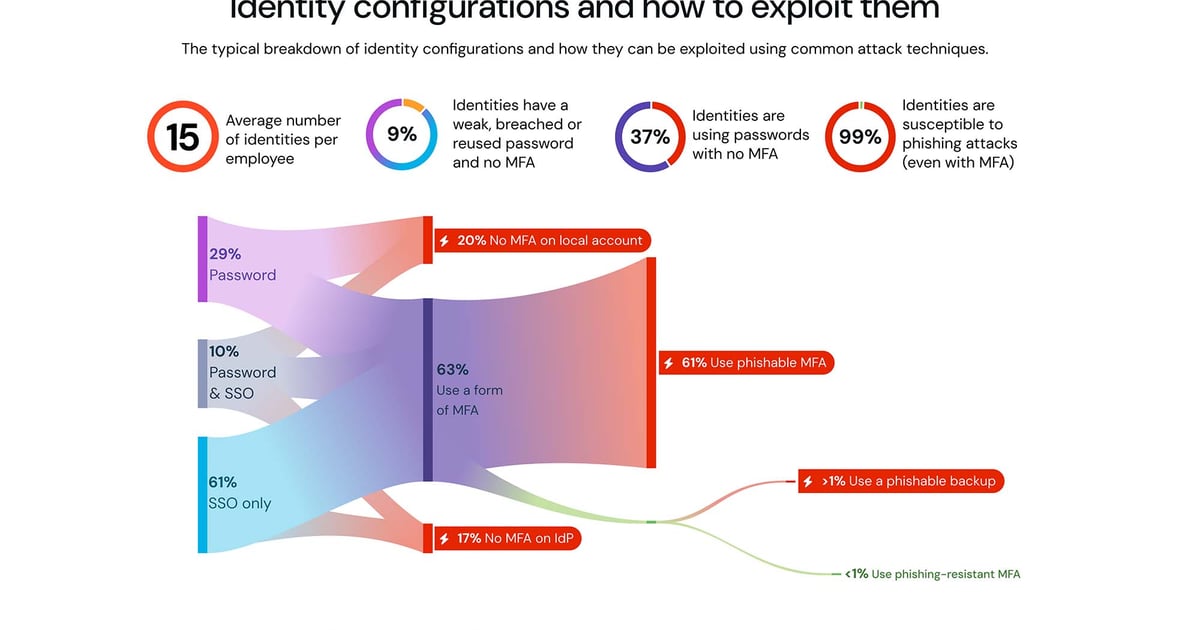
– Average employee has 15 identities, with 37% using password-based logins without MFA.
– 61% of accounts use only SSO, while 29% rely solely on passwords; only 10% utilize both SSO and passwords.
– 63% of accounts employ some form of MFA, but most are vulnerable to phishing attacks (“phishable MFA”).
– Less than 1% of accounts with SSO utilize “phishing-resistant MFA.”
5. **Issues with Password Usage**:
– 80% of password-only accounts lack MFA.
– 40% of accounts with both SSO and passwords do not have MFA, risking ghost logins and higher vulnerability.
6. **Identity Provider Vulnerabilities**:
– 17% of identity provider accounts lack MFA.
– 10% reuse passwords, increasing the risk of account compromise if the password is stolen.
7. **Critical Accounts and MFA**: Identity provider accounts are crucial, yet 20% lack MFA, exposing them to significant risk.
8. **Concerns about Weak Passwords**:
– 9% of identities use breached, weak, or reused passwords without MFA, making them highly susceptible to attacks such as credential stuffing and phishing attempts.
### Action Items:
– Review and enhance identity management policies.
– Increase investment in MFA and consider deploying phishing-resistant methods.
– Conduct a thorough audit of current accounts and access methods to identify vulnerabilities.
– Educate employees on the importance of strong passwords and the risks associated with reuse and lack of MFA.