October 22, 2024 at 12:31PM
Lumma Stealer has launched a campaign using malicious CAPTCHA pages to prompt malware downloads. This malware aims to steal sensitive data. Researchers emphasize the need for security teams to adopt continuous monitoring and adapt defenses against evolving threats like Lumma Stealer, using a multilayered approach for effective protection.
### Meeting Takeaways on Lumma Stealer Campaign
1. **Overview of Lumma Stealer**:
– Lumma Stealer is a Malware-as-a-Service (MaaS) commonly used to steal sensitive information such as passwords and cryptocurrency wallet data.
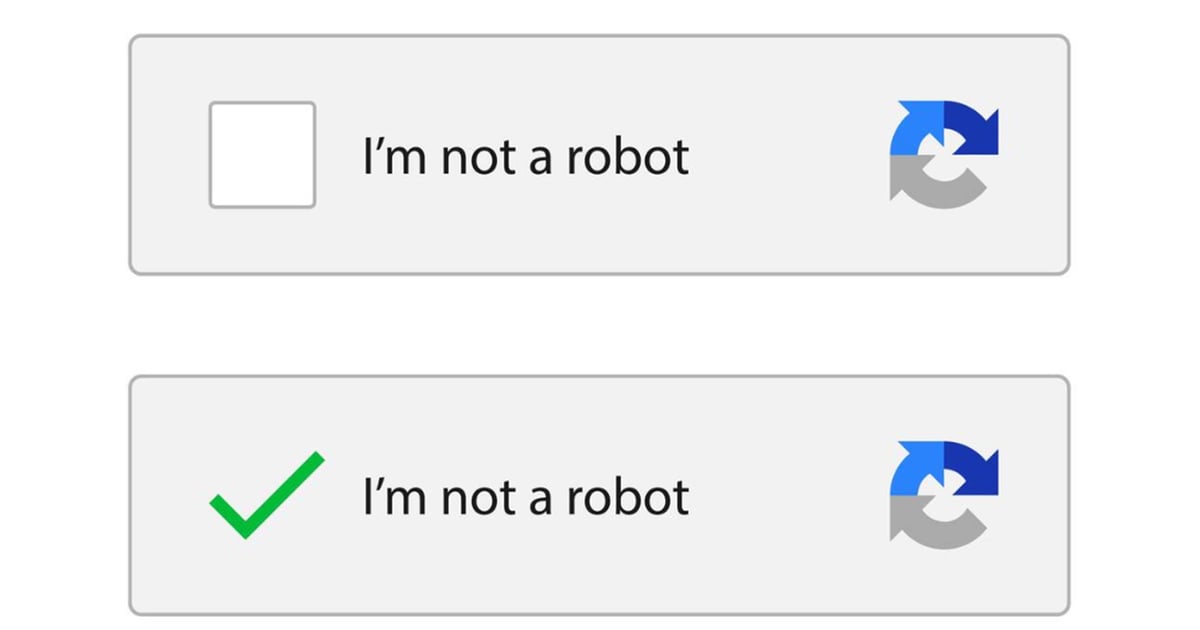
2. **New CAPTCHA Scamming Technique**:
– A new campaign employs malicious CAPTCHA pages to trick targets into clicking through a “verification” process that initiates malware downloads upon clicking “I’m not a robot.”
3. **Execution of Malicious Commands**:
– Completing CAPTCHA verification triggers a PowerShell command, leading to the download of initial malware onto the victim’s machine.
4. **Adaptability of Lumma Stealer**:
– The campaign has shown diverse tactics over the years, including:
– YouTube channels offering software workarounds (January 2024).
– Facebook ads luring users to download a seemingly legitimate AI photo editor (Summer 2024).
– Targeting popular games like Hamster Kombat to distribute malware.
5. **Evolving Threat Landscape**:
– The investigation highlights Lumma Stealer’s capability to adapt and evade detection, necessitating sophisticated tactics that mix legitimate software with deceptive delivery methods.
6. **Need for Collaborative Defense**:
– Effective protection against Lumma Stealer demands close cooperation among threat intelligence, Security Operations Centers (SOCs), and incident-response teams.
7. **Continuous Monitoring and Adaptation**:
– Security teams must engage in ongoing monitoring, update detection rules and security controls, and employ a multilayered defense strategy to combat evolving threats like Lumma Stealer.
8. **Expert Insight**:
– Sarah Jones emphasizes the importance of a proactive approach that includes advanced technical controls and continuous threat hunting to counteract sophisticated malware campaigns effectively.
This summary encapsulates the key points discussed regarding the Lumma Stealer campaign and highlights the ongoing challenges and necessary responses from security teams.