November 6, 2024 at 08:06AM
The SANS 2024 report reveals a rise in attacks on industrial control systems, with 74.4% of incidents being non-ransomware related. Key attack vectors include remote services and supply chain compromises. While ransomware incidents are relatively low (12%), their impact on ICS/OT environments remains severe, affecting reliability and safety.
**Meeting Takeaways: State of ICS/OT Cybersecurity 2024 Report**
1. **Increase in Attacks**: There is a notable rise in attacks targeting industrial control systems (ICS) and operational technology (OT) systems, with adversaries exploiting vulnerabilities in IT networks to infiltrate OT networks.
2. **Incident Statistics**:
– Non-ransomware incidents constitute 74.4% of reported cases, while ransomware incidents account for 11.7%.
– 19% of cybersecurity professionals reported experiencing one or more security incidents in the past year.
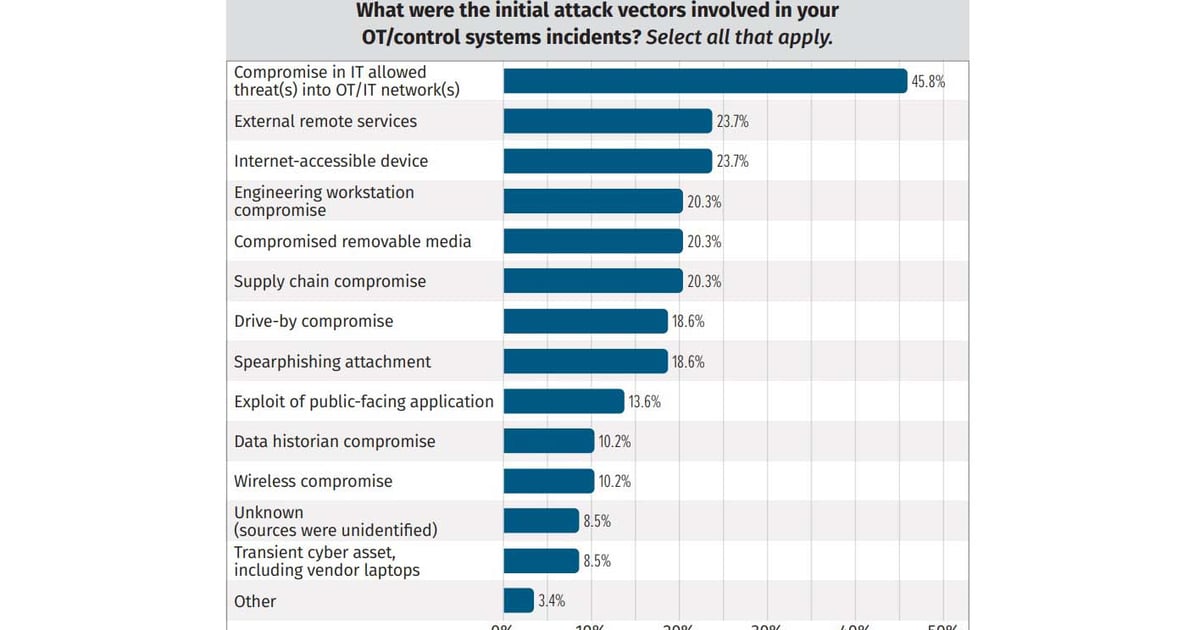
3. **Initial Attack Vectors**: Key methods for initial compromises include:
– External remote services and internet-accessible devices (23.7%)
– Employee workstations (20.3%)
– Removable media (20.3%)
– Supply chain compromises (20.3%)
– Spear phishing attempts (18.6% with email attachments)
4. **Ransomware Impact**:
– Only 12% of respondents reported ransomware attacks, yet the potential consequences are severe.
– Among organizations hit by ransomware:
– 38% reported only IT systems were affected.
– 28.6% indicated impact on both OT and ICS networks.
– 21% experienced disruptions across both networks.
– Over a third (38.1%) noted a compromise in reliability and safety due to these attacks.
5. **Response Consideration**: Despite a perceived decrease in ransomware trends, the report emphasizes that the risks remain significant and must be factored into incident response strategies specific to ICS/OT environments.
**Recommendation**: Enhance incident response programs to address the evolving threat landscape in ICS/OT environments and prioritize cybersecurity training to mitigate potential attack vectors.